DeadSec CTF2024
Misc
Welcome
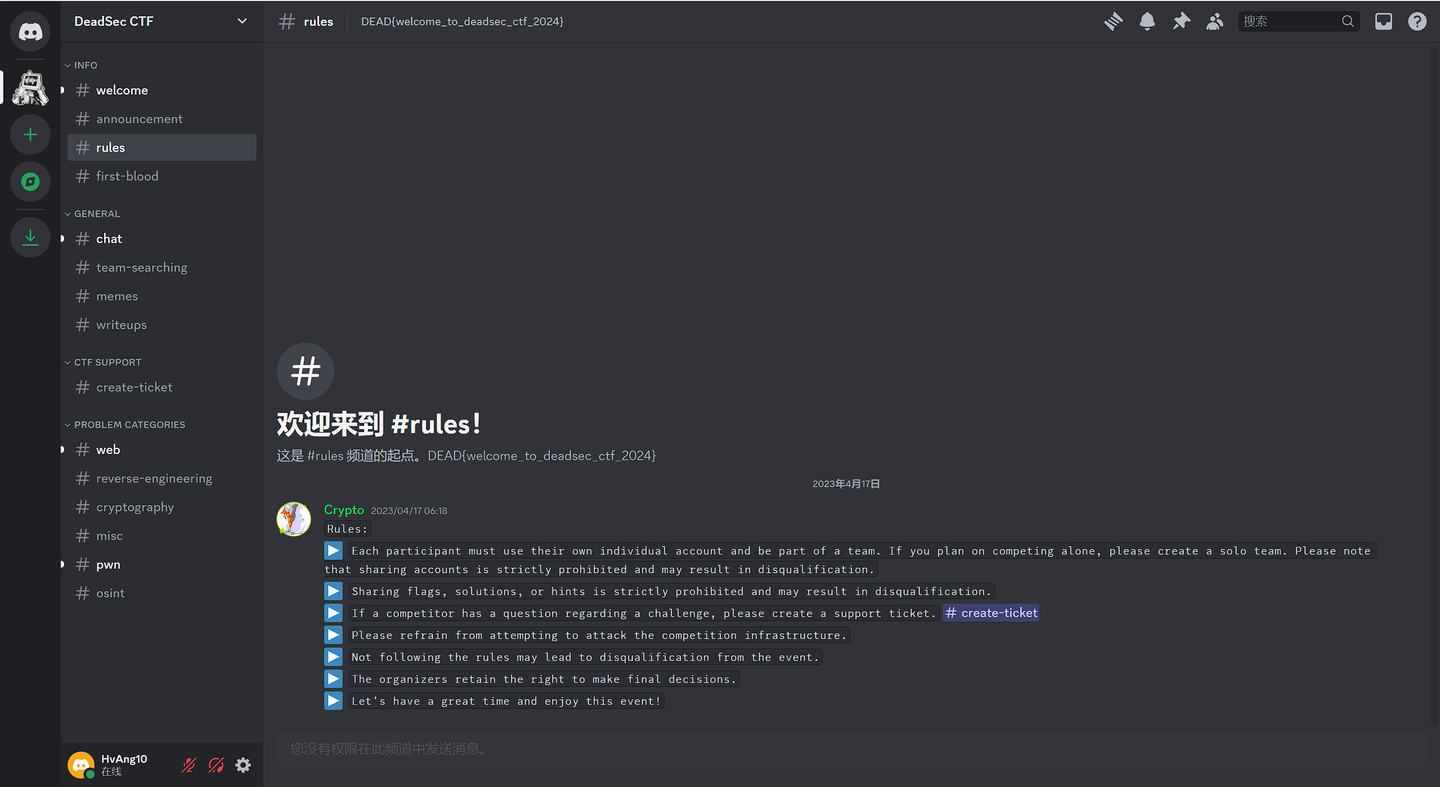
Mic check
简单,写个脚本交互100次就行了
from pwn import * |
MAN in the middle
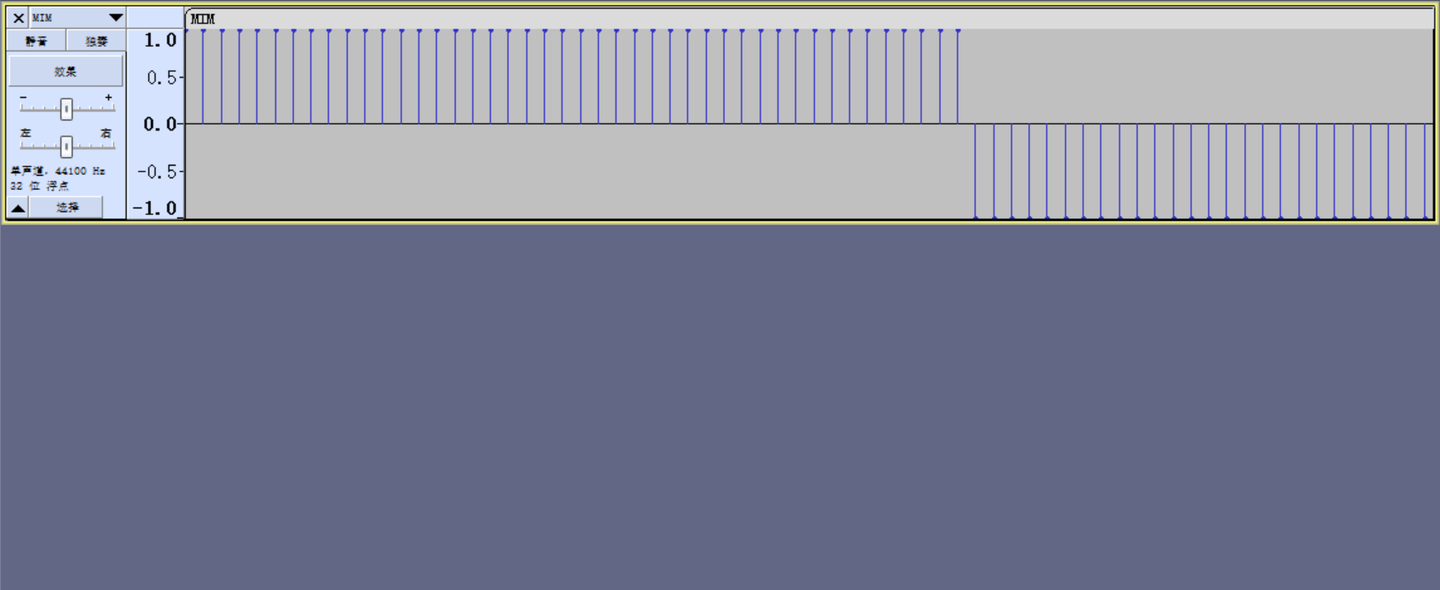
可以看到只有上下两个波形,二进制?最后那一段可以忽略不看
但是数据量好大,手动提不现实
010查看16进制,发现FF 7F*44,算一段,01 80*44也算作一段
前者为1,后者为0,解不出来,尝试01为1,10为0
from Crypto.Util.number import * |
manchester encoding is a method of encoding digital data in which each bit of data is represented by two voltage levels, ensuring a transition at the middle of each bit period. this transition serves as both a clock and data signal, making it highly effective for synchronous communication. developed by g. e. thomas, manchester encoding is widely used in various communication protocols, including ethernet. its primary advantage lies in its robustness against timing errors and ease of clock recovery, as the regular transitions enable the receiver to maintain synchronization with the transmitter. by embedding the clock signal within the data stream, manchester encoding mitigates the risk of synchronization loss, making it a reliable choice for high-speed digital data transmission. and here is your flag: dead{m4nch3573r_4_7h3_w1n} good job! |
Forgotten Password()
generate.py
from io import BytesIO |
然后附件就是一个加密文件
开眼了https://blog.csdn.net/qq_42880719/article/details/140753854
Crypto
flag killer
#!/usr/bin/python3 |
注意到flag[index:index+3],flag = hexlify(b'DEAD{test}').decode(),output是以五位一组的,我们可以通过0xfff爆破一手
from Crypto.Util.number import * |
444541447b3236336638373165383830653964633764323430313030303330346663363065393863376335383807d
0x7d是},最后的07d->7d即可
Raul Rosas
from Crypto.Util.number import * |
一开始还在想n1,n2之间的联系,发现,除了p2的高位是p1的前605位之外,没有任何可以利用的地方,当时没有思路,瞄了一眼,发现还得是展开,不展开没法做这种题
from Crypto.Util.number import * |
也可以,获取p1的高位,然后Coppersmith
p2 = gmpy2.iroot(n2//q2, 2)[0] |
# sage |
Web
Bing2
6,我说怎么没有源代码的呢
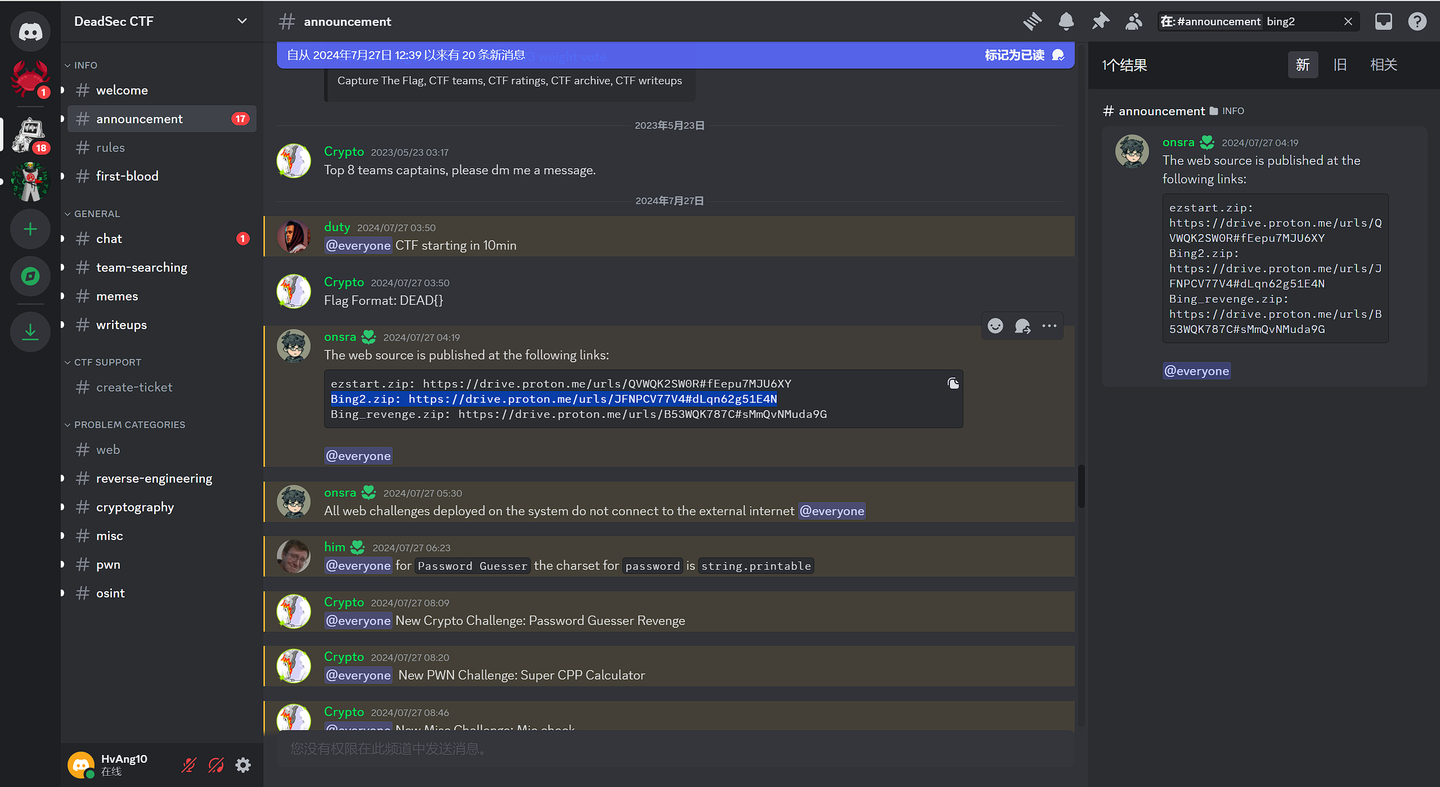
喜欢放Discord是吧,我结束才发现。。。
还好题目环境还在
ezstart.zip: https://drive.proton.me/urls/QVWQK2SW0R#fEepu7MJU6XY |
bing.php
|
可见过滤了一大堆,命令拼接符也被过滤了很多
就是这个的升级版
https://www.cnblogs.com/qiushuo/p/17487444.html#command-injection
%0a换行符,需要php环境 |
测试发现%0a可用,\n也能用,学到了
import requests |
bing_revenge
app.py
#!/usr/bin/env python3 |
output = os.system(f'ping -c 4 {cmd}'),这里没有输出了,但也没有过滤了,哦豁
想起个docker,看看能不能反弹shell,但是.sh的我不会起………………
ezstart()
upload.php
|