UIUCTF2024
Crypto
X Marked the Spot
题目
from itertools import cycle |
简单的异或算法
根据uiuctf{}拿到key,因为我们一开始就可以获取到key的前七位,而正好flag的长度为48,所以最后的},可以帮我们确认key的最后一位
from pwn import * |
Without a Trace
题目
import numpy as np |
分析一下代码,我们输入5*5矩阵的对角元素,同时这个矩阵会被check,flag分为5部分,也排布在5*5矩阵的对角上,然后两个矩阵相乘,最后返回轨迹,即对角线上的元素之和
由于检测的存在,不能直接获取到一部分的flag,但可以通过运算或得
发送6次对角元素,直接手动交互
[ |
简单题
from Crypto.Util.number import * |
Naptime
题目
from random import randint |
一开始我还想,逆推加密函数,根据ct在a中的加算组合,来确定flag的二进制序列,发现GPT写的回溯算法应该是行不通的,然后看了一下群里师傅的思路,又再仔细读了一下代码,下面是我的思路
可以看到给出了加解密函数,还有一些辅助函数,如果我们可以得到参数b,pi,M,W,那么就可以利用解密函数来解密密文了
pi = np.random.permutation(list(i for i in range(len(b)))).tolist(),是一个排列组合,可以用b来爆破一手,那么缺的就是三个参数了
通过读懂程序,我们可以判断到M和W的位数,然后根据题目提供的a,爆破出M和W的可能取值,b的话得重新生成,再进行递增排序(根据生成b的函数可知)
恰好拿到的第一组M和W,以及根据pi爆破flag,得到了正确的flag
from random import randint |
后来看到了狼组的wp,发现还真可以用背包问题求解,但是我不会写,下面是他们的wp
from Crypto.Util.number import * |
Determined
看题目貌似是算行列式(det)?
from Crypto.Util.number import bytes_to_long, long_to_bytes |
def fun(M): |
此处的fun()应该是用来计算五阶行列式的
因为我们可以控制元素为0,所以我们可以控制想要的行列式值
我们可以计算这样的一个矩阵的行列式
[ |
按一二行展开,就成了计算
[ |
则Det(M)=-p*r
gcd一下n,便可得到p
from Crypto.Util.number import * |
Crypto(未解)
以下由于时间关系,或者说难度,就暂时没有做了
Snore Signatures
题目
#!/usr/bin/env python3 |
These signatures are a bore! |
Groups
题目
from random import randint |
My friend told me that cryptography is unbreakable if moduli are Carmichael numbers instead of primes. I decided to use this CTF to test out this theory. |
Key in a Haystack
题目
from Crypto.Util.number import getPrime |
I encrpyted the flag, but I lost my key in an annoyingly large haystack. Can you help me find it and decrypt the flag? |
Web
Fare Evasion()
靶机地址
https://fare-evasion.chal.uiuc.tf/
逃票
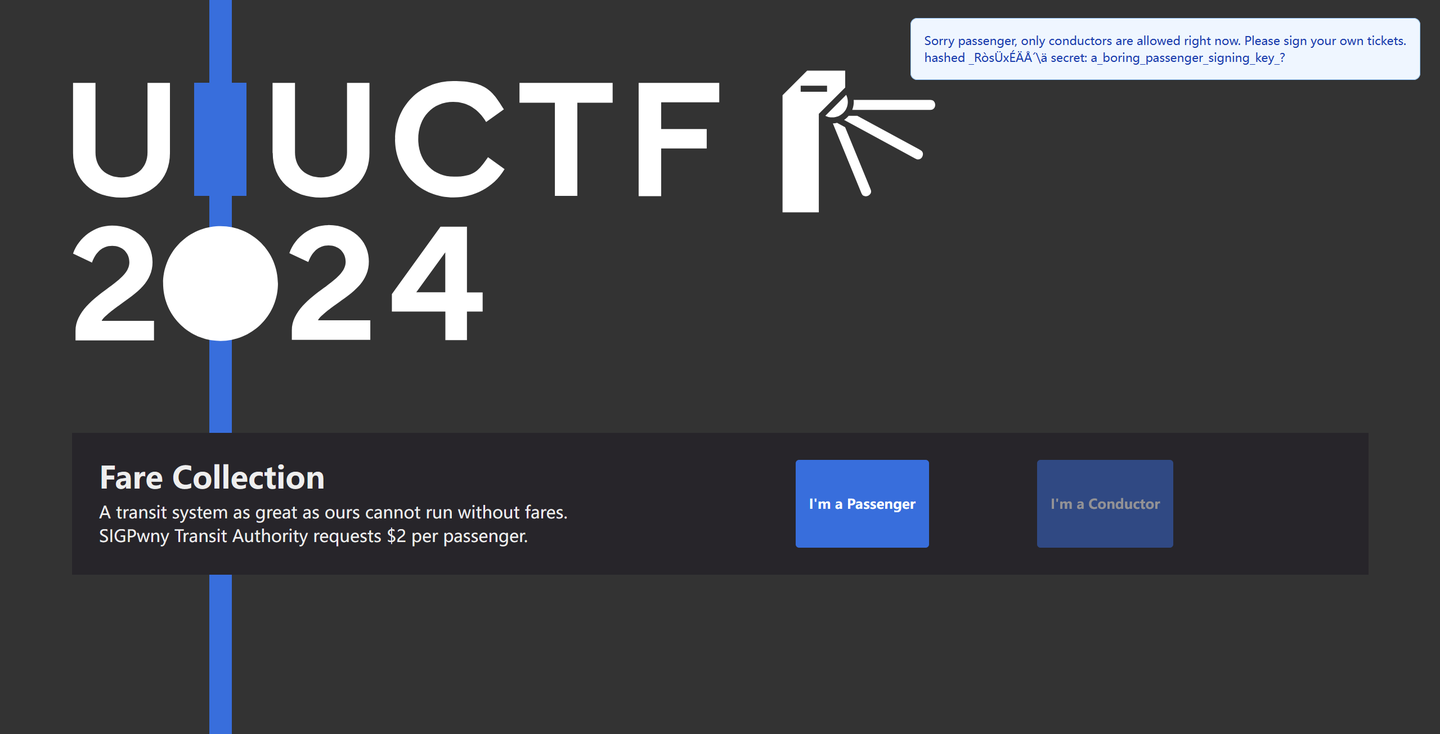
感觉是JWT伪造,试了一下,好像也不是啊

看一眼前端这个buttonI'm a Conductor,改了一下,没有用
async function pay() { |
然后,是这个pay()函数
这里的sql注入和md5应该是有用处的,从返回的包的结果来看,思路应该还是要回到JWT伪造上,然后卡住……
Web又没得玩。。。。。
然后这misc好像确实是有难度的,不用打了,下班
又是只能做做密码的一天…………